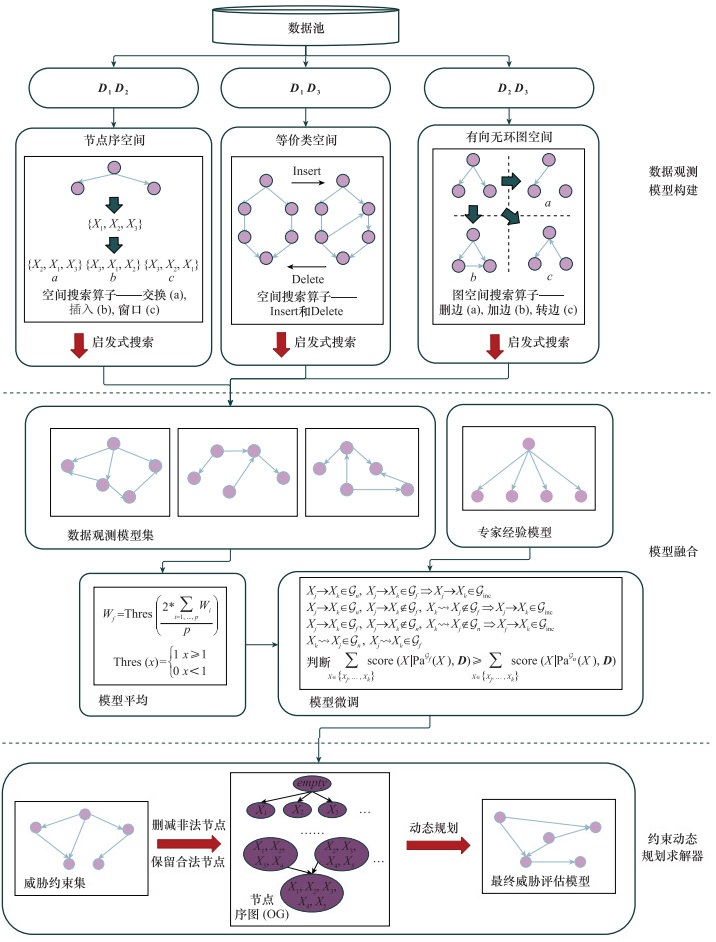
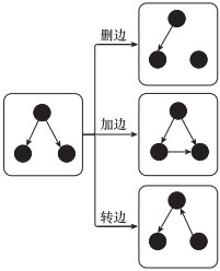
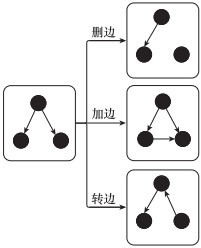
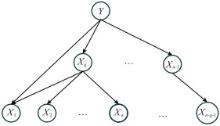
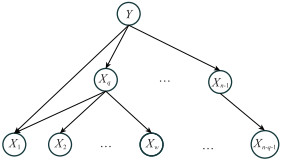
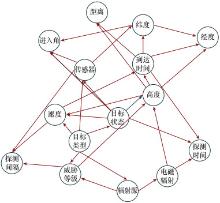
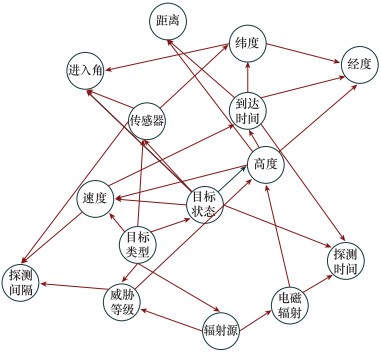
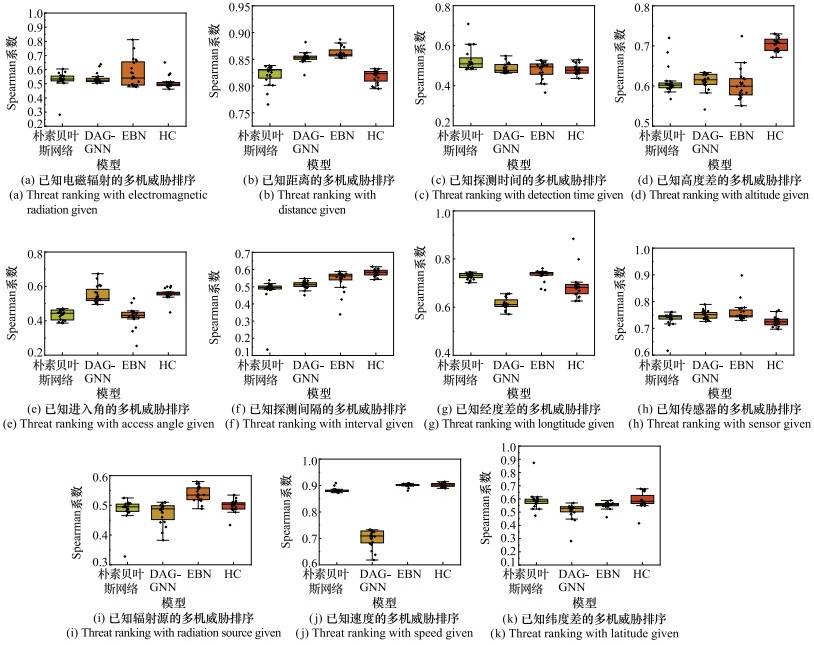
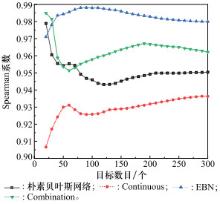
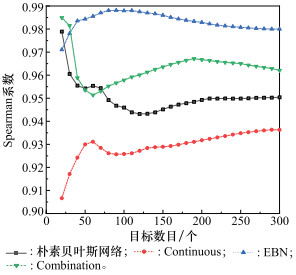
Systems Engineering and Electronics ›› 2024, Vol. 46 ›› Issue (2): 586-598.doi: 10.12305/j.issn.1001-506X.2024.02.22
• Systems Engineering • Previous Articles
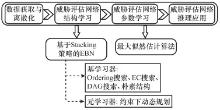
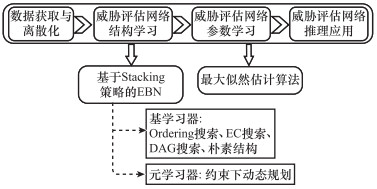
Target threat assessment based on ensemble Bayesian network with Stacking strategy
Zidong WANG, Xiaoguang GAO, Xiaohan LIU
- School of Electronics and Information, Northwestern Polytechnical University, Xi'an 710129, China
-
Received:2022-12-16Online:2024-01-25Published:2024-02-06 -
Contact:Xiaoguang GAO
CLC Number:
Cite this article
Zidong WANG, Xiaoguang GAO, Xiaohan LIU. Target threat assessment based on ensemble Bayesian network with Stacking strategy[J]. Systems Engineering and Electronics, 2024, 46(2): 586-598.
share this article
Table 1
Statement for threat datafield"
| 字段 | 威胁数据 | 字段说明 |
| 探测段 | latitude | 纬度 |
| longitude | 经度 | |
| altitude | 高度/m | |
| angle | 进入角 | |
| speed | 速度/(n mile/h) | |
| duration | 探测持续时间/s | |
| detected | 是否发现电磁辐射 | |
| sources | 电磁辐射源推断 | |
| sensors | 探测到目标的红方源传感器 | |
| interval | 探测到目标的时间与当前时刻间隔 | |
| distance | 目标与红方源传感器的估计距离 | |
| 真实段 | type | 目标类型 |
| latitude | 纬度 | |
| longitude | 经度 | |
| altitude | 高度/m | |
| angle | 进入角 | |
| speed | 速度/(n mile/h) | |
| state | 当前任务状态 |
Table 2
States and discretization result of threat data"
| 节点 | 状态空间及离散化 |
| 威胁等级 | 3:“低威胁”; 2:“中威胁”; 1:“高威胁”; 0:“假目标” |
| 目标类型 | 5:“导弹”; 4:“非隐身舰载攻击机”; 3:“电子战飞机”; 2:“无人机”; 1:“隐身舰载攻击机”; 0:“假目标” |
| 目标状态 | 2:“非RTB”; 1:“RTB”; 0:“假目标” |
| 到达时间 | 4:“较长”; 3:“长”; 2:“中等”; 1:“较短”; 0:“短” |
| 电磁辐射 | 1:“探测到电磁辐射”; 0: “未探测到电磁辐射” |
| 辐射源 | 2:“机载有源相控阵雷达”; 1:“干扰器”; 0:“未探测到辐射” |
| 探测时间 | 2:“探测时间较长”; 1:“探测时间较短”; 0: “未探测到电磁辐射” |
| 高度差 | 4:“较高”; 3:“高”; 2:“中”; 1:“较低”; 0:“低” |
| 传感器 | 4:“其他”; 3:“有源相控阵雷达”; 2:“对空搜索雷达”; 1:“电子战装备”; 0:“电子支援/测量系统” |
| 探测间隔 | 2:“长”; 1:“中”; 0:“短” |
| 进入角 | 2:“大”; 1:“中”; 0:“小” |
| 纬度差 | 4:“大”; 3:“较大”; 2:“中”; 1:“较小”; 0:“小” |
| 经度差 | 4:“大”; 3:“较大”; 2:“中”; 1:“较小”; 0:“小” |
| 速度 | 4:“快”; 3:“较快”; 2:“中”; 1:“较慢”; 0:“慢” |
| 距离 | 4:“远”; 3:“较远”; 2:“中”; 1:“较近”; 0:“近” |
Table 3
Sensitive analysis for threat level in EBN model"
| 威胁要素 | 方差减少量 | VR/% | 互信息减少量 | MI/% |
| 威胁等级 | 0.511 70 | 100 | 1.100 67 | 100 |
| 目标类型 | 0.451 70 | 88.3 | 0.840 98 | 76.4 |
| 目标状态 | 0.373 30 | 73 | 0.504 96 | 45.9 |
| 进入角 | 0.242 00 | 47.3 | 0.285 25 | 25.9 |
| 距离 | 0.239 20 | 46.7 | 0.450 32 | 40.9 |
| 速度 | 0.234 50 | 45.8 | 0.412 87 | 37.5 |
| 到达时间 | 0.230 80 | 45.1 | 0.457 28 | 41.5 |
| 经度差 | 0.179 60 | 35.1 | 0.295 20 | 26.8 |
| 纬度差 | 0.156 90 | 30.7 | 0.242 40 | 22 |
| 高度差 | 0.108 60 | 21.2 | 0.273 10 | 24.8 |
| 传感器 | 0.098 62 | 19.3 | 0.274 18 | 24.9 |
| 探测间隔 | 0.059 47 | 11.6 | 0.114 46 | 10.4 |
| 辐射源 | 0.050 32 | 9.83 | 0.189 58 | 17.2 |
| 探测时间 | 0.037 74 | 7.37 | 0.165 71 | 15.1 |
| 电磁辐射 | 0.036 15 | 7.06 | 0.163 73 | 14.9 |
Table 4
Sensitive analysis for arrive time in EBN model"
| 威胁要素 | 方差减少量 | VR/% | 互信息减少量 | MI/% |
| 到达时间 | 2.025 0 | 100 | 2.348 11 | 100 |
| 速度 | 1.643 0 | 81.1 | 1.201 66 | 51.2 |
| 距离 | 1.471 0 | 72.7 | 0.937 75 | 39.9 |
| 目标类型 | 1.299 0 | 64.1 | 0.804 42 | 34.3 |
| 传感器 | 1.267 0 | 62.6 | 0.710 10 | 30.2 |
| 经度差 | 1.214 0 | 60 | 0.712 61 | 30.3 |
| 高度差 | 0.893 6 | 44.1 | 0.593 58 | 25.3 |
| 威胁等级 | 0.831 0 | 41 | 0.457 28 | 19.5 |
| 纬度差 | 0.799 0 | 39.5 | 0.440 98 | 18.8 |
| 探测时间 | 0.751 3 | 37.1 | 0.383 31 | 16.3 |
| 辐射源 | 0.750 7 | 37.1 | 0.380 81 | 16.2 |
| 电磁辐射 | 0.750 2 | 37.1 | 0.378 54 | 16.1 |
| 探测间隔 | 0.699 0 | 34.5 | 0.327 07 | 13.9 |
| 目标状态 | 0.393 2 | 19.4 | 0.263 62 | 11.2 |
| 进入角 | 0.253 7 | 12.5 | 0.173 17 | 7.37 |
Table 5
Comparison of standard dataset score"
| 数据集 | N | PC | HC | DAG-GNN | EBN |
| Asia | 8 | -2 429.5 | -2 344.8 | -2 480.3 | -2 344.8 |
| Sachs | 11 | -8 666.2 | -7 784.5 | -9 188.9 | -7 751.4 |
| Child | 20 | -14 240.2 | -12 824.2 | -15 902.4 | -12 772.8 |
| Insurance | 27 | -16 448.9 | -14 729.0 | -21 415.6 | -14 828.4 |
| Alarm | 37 | -17 046.6 | -12 777.9 | -16 027.8 | -11 990.6 |
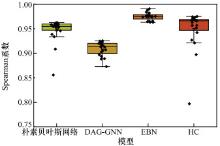
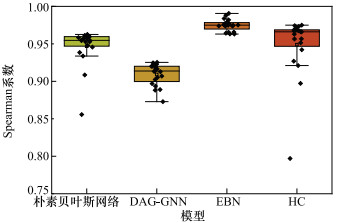
Table 7
Difference in inference probabilities in different models for threat level and arrival time under a signle set of evidence"
| 参数 | 威胁等级 | 到达时间 | |||||||||
| 朴素贝叶斯网络 | PC | DAG-GNN | EBN | HC | 朴素贝叶斯网络 | PC | DAG-GNN | EBN | HC | ||
| 高度差 | 0.385 278 | 0.429 249 | 0.451 740 | 0.366 072 | 0.376 139 | 0.721 771 | 0.800 701 | 0.720 733 | 0.664 939 | 0.664 939 | |
| 电磁辐射 | 0.383 344 | 0.429 249 | 0.480 233 | 0.383 344 | 0.383 344 | 0.800 701 | 0.800 701 | 0.749 012 | 0.686 395 | 0.686 378 | |
| 距离 | 0.429 249 | 0.429 249 | 0.440 272 | 0.285 221 | 0.285 239 | 0.534 486 | 0.800 701 | 0.644 175 | 0.535 222 | 0.535 392 | |
| 探测时间 | 0.383 304 | 0.429 249 | 0.513 619 | 0.383 253 | 0.383 228 | 0.800 701 | 0.800 701 | 0.799 731 | 0.686 107 | 0.686 032 | |
| 进入角 | 0.340 331 | 0.429 249 | 0.438 985 | 0.335 783 | 0.338 974 | 0.800 701 | 0.800 701 | 0.789 385 | 0.755 651 | 0.754 664 | |
| 探测间隔 | 0.386 872 | 0.429 249 | 0.464 123 | 0.393 855 | 0.396 456 | 0.800 701 | 0.800 701 | 0.772 372 | 0.714 331 | 0.714 923 | |
| 经度差 | 0.429 249 | 0.429 249 | 0.458 565 | 0.331 653 | 0.340 466 | 0.689 197 | 0.800 701 | 0.762 617 | 0.689 216 | 0.699 463 | |
| 纬度差 | 0.429 249 | 0.429 249 | 0.388 884 | 0.313 799 | 0.310 357 | 0.607 899 | 0.800 701 | 0.640 820 | 0.607 882 | 0.609 035 | |
| 传感器 | 0.361 617 | 0.429 249 | 0.498 137 | 0.362 306 | 0.362 873 | 0.800 701 | 0.800 701 | 0.727 468 | 0.601 639 | 0.601 778 | |
| 辐射源 | 0.364 222 | 0.429 249 | 0.476 725 | 0.364 222 | 0.364 222 | 0.800 701 | 0.800 701 | 0.782 533 | 0.683 139 | 0.683 084 | |
| 速度 | 0.429 249 | 0.429 249 | 0.394 085 | 0.299 607 | 0.310 927 | 0.445 926 | 0.800 701 | 0.497 182 | 0.445 926 | 0.445 926 | |
Table 8
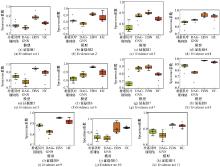
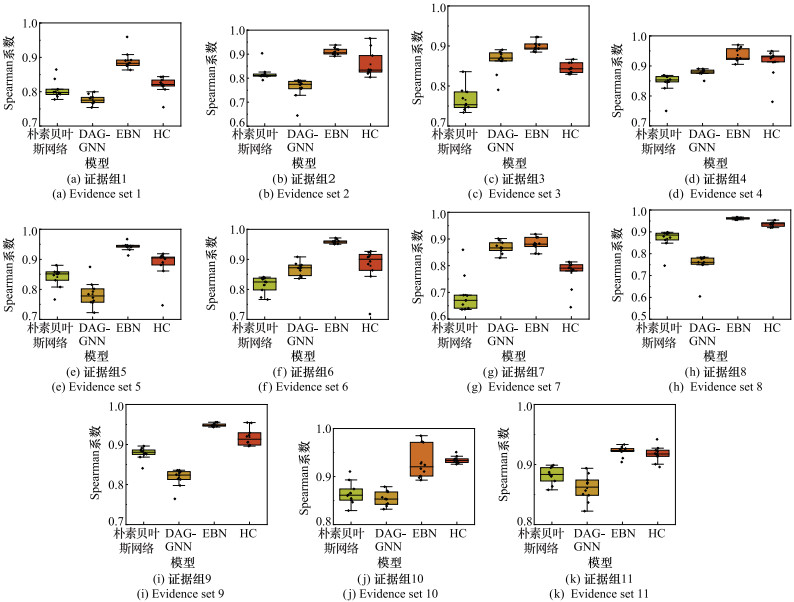
Inference probability difference for threat level and arrival time in different models (five sets of evidence)"
| 证据 | 威胁等级 | 到达时间 | |||||||||
| 朴素贝叶斯 | PC | DAG-GNN | EBN | HC | 朴素贝叶斯 | PC | DAG-GNN | EBN | HC | ||
| 证据1 | 0.159 421 | 0.394 450 | 0.297 223 | 0.050 815 | 0.074 805 | 0.542 848 | 0.802 661 | 0.673 253 | 0.382 580 | 0.425 889 | |
| 证据2 | 0.245 926 | 0.367 699 | 0.280 798 | 0.161 683 | 0.174 557 | 0.501 894 | 0.800 701 | 0.571 084 | 0.450 121 | 0.473 529 | |
| 证据3 | 0.227 890 | 0.367 699 | 0.274 376 | 0.087 386 | 0.123 591 | 0.373 738 | 0.800 701 | 0.454 633 | 0.317 384 | 0.317 139 | |
| 证据4 | 0.213 945 | 0.367 699 | 0.264 074 | 0.119 122 | 0.140 500 | 0.533 755 | 0.800 701 | 0.570 959 | 0.370 088 | 0.394 754 | |
| 证据5 | 0.324 179 | 0.367 699 | 0.272 611 | 0.182 001 | 0.198 085 | 0.319 811 | 0.800 701 | 0.374 741 | 0.218 398 | 0.219 299 | |
| 证据6 | 0.219 736 | 0.367 699 | 0.299 184 | 0.077 517 | 0.109 667 | 0.219 736 | 0.367 699 | 0.299 184 | 0.077 517 | 0.109 667 | |
| 证据7 | 0.245 919 | 0.367 699 | 0.188 111 | 0.168 335 | 0.174 557 | 0.532 106 | 0.800 701 | 0.483 979 | 0.472 498 | 0.473 529 | |
| 证据8 | 0.301 390 | 0.367 699 | 0.287 009 | 0.222 570 | 0.240 042 | 0.660 765 | 0.800 701 | 0.616 670 | 0.4731 66 | 0.488 209 | |
| 证据9 | 0.337 279 | 0.367 699 | 0.210 973 | 0.195 132 | 0.202 970 | 0.319 811 | 0.800 701 | 0.344 881 | 0.222 098 | 0.225 807 | |
| 证据10 | 0.226 210 | 0.367 699 | 0.201 543 | 0.156 268 | 0.162 545 | 0.352 037 | 0.800 701 | 0.353 908 | 0.262 630 | 0.262 725 | |
| 证据11 | 0.210 302 | 0.367 699 | 0.263 390 | 0.068 759 | 0.103 292 | 0.294 595 | 0.800 701 | 0.359 207 | 0.267 841 | 0.266 736 | |
| 1 | LIEBHABER M J, FEHER B. Air threat assessment: research, model, and display guidelines[R]. San Diego: Space and Naval Warfair Systems Command, 2002. |
| 2 | SCHUCK T , BLASCH E . OODA Loop 2.0: information not agility is life[M]. New York: Breaking Defense, 2017. |
| 3 | HINMAN M. Some computational approaches for situation assessment and impact assessment[C]//Proc. of the 5th International Conference on Information Fusion, 2022: 687-693. |
| 4 | YU D, WANG H J, YUAN H Y. Method of unknow target risk analysis and threat assessment for UUVs[C]//Proc. of the 39th Chinese Control Conference, 2020: 594-599. |
| 5 |
LUO R N , HUANG S C , ZHAO Y , et al. Threat assessment method of low altitude show small (LSS) targets based on information entropy and AHP[J]. Entropy, 2021, 23 (10): 1292- 1304.
doi: 10.3390/e23101292 |
| 6 | PAWLAK Z . Rough sets[J]. International Journal of Computer and Information Sciences, 1982, 11 (2): 341- 356. |
| 7 | DENG Y . A threat assessment model under uncertain environment[J]. Mathematical Problems in Engineering, 2015, 2015 (15): 878024. |
| 8 |
EHASN A , JAVAD H . Target threat assessment using fuzzy sets theory[J]. International Journal of Advances in Intelligent Informatics, 2015, 1 (2): 57- 74.
doi: 10.26555/ijain.v1i2.18 |
| 9 |
BEHZADIAN M , OTAGHSARA S K , YAZDANI M , et al. A state-of the-art survey of TOPSIS applications[J]. Expert Systems with Applications, 2012, 39 (17): 13051- 13069.
doi: 10.1016/j.eswa.2012.05.056 |
| 10 | FAN Z P , ZHANG X , CHEN F D , et al. Extended TODIM method for hybrid multiple attribute decision making problems[J]. Knowledge-Based Systems, 2013, 43 (4): 40- 48. |
| 11 |
JIANG Y P , LIANG X , LIANG H M . An I-TODIM method for multi-attribute decision making with interval numbers[J]. Soft Computing, 2017, 21 (18): 5489- 5506.
doi: 10.1007/s00500-016-2139-5 |
| 12 | HAUTANIEMI S K , KORPISAARI P T , SAARINEN J P P . Target identification with dynamic hybrid Bayesian networks[J]. Proc.of SPIE-The International Society for Optical Engineering, 2002, 4170, 92- 102. |
| 13 | HAUTANIEMI S K , SAARINEN J P P , DASARATHY B V . Multitarget tracking with IMM and Bayesian networks: empi-rical studies[J]. Proc.of SPIE-The International Society for Optical Engineering, 2001, 4385, 47- 57. |
| 14 | 陈龙, 马亚平. 基于分层贝叶斯网络的航母编队对潜威胁评[J]. 系统仿真学报, 2017, 29 (9): 2206-2212, 2220. |
| CHEN L , MA Y P . Threat assessment of aircraft carrier formation based on hierarchical Bayesian network[J]. Journal of System Simulation, 2017, 29 (9): 2206-2212, 2220. | |
| 15 | 高晓光, 杨宇. 基于贝叶斯网的舰艇防空威胁评估[J]. 战术导弹技术, 2020, (4): 47-57, 70. |
| GAO X G , YANG Y . Threat assessment for warship air defense Based on Bayesian network[J]. Tactical Missile Technology, 2020, (4): 47-57, 70. | |
| 16 | 刘振, 彭军, 胡云安. 一种新型动态贝叶斯网络及其在威胁评估中的应用[J]. 火力与指挥控制, 2014, 39 (2): 16- 20. |
| LIU Z , PENG J , HU Y A . A new kind dynamic Bayesian network and application to threat1 assessment[J]. Fire Control & Command Control, 2014, 39 (2): 16- 20. | |
| 17 | 李旭辉, 顾颖彦, 韩兴豪. 基于动态云贝叶斯网络的舰艇防空目标威胁评估[J]. 舰船电子对抗, 2021, 44 (1): 38- 44. |
| LI X H , GU Y Y , HAN X H . Threat assessment of ship air defense target based on dynamic cloud Bayesian network[J]. Shipboard Electronic Countermeasure, 2021, 44 (1): 38- 44. | |
| 18 | 孟光磊, 龚光红. 基于混合贝叶斯网的空域目标威胁评估方法[J]. 系统工程与电子技术, 2010, 32 (11): 2398- 2401. |
| MENG G L , GONG G H . Threat assessment of aerial targets based on hybrid Bayesian network[J]. Systems Engineering and Electronics, 2010, 32 (11): 2398- 2401. | |
| 19 | PEARL J . Models, reasoning and inference[M]. Cambridge: Cambridge University Press, 2000. |
| 20 | LEE C, VAN B P. Metaheuristics for score-and-search Bayesian network structure learning[C]//Proc. of the 30th Canadian Conference on Artificial Intelligence, 2017: 129-141. |
| 21 | SCANAGATTA M, CORANI G, ZAFFALON M. Improved local search in Bayesian networks structure learning[C]//Proc. of the 3rd International Workshop on Advanced Methodologies for Bayesian Networks, 2017: 45-56. |
| 22 | CONSTANTINOU A C . Learning Bayesian networks with the Saiyan algorithm[J]. ACM Transactions on Knowledge Discovery from Data, 2020, 14 (4): 1- 21. |
| 23 |
CONSTANTINOU A C , LIU Y , KITSON N K , et al. Effective and efficient structure learning with pruning and model averaging strategies[J]. International Journal of Approximate Reasoning, 2022, 151, 292- 321.
doi: 10.1016/j.ijar.2022.09.016 |
| 24 |
RAMSEY J D , GLYMOUR M , SANCHEZ-ROMERO R , et al. A million variables and more: the fast greedy equivalence search algorithm for learning high-dimensional graphical causal models, with an application to functional magnetic resonance images[J]. International Journal of Data Science and Analytics, 2017, 3 (2): 121- 129.
doi: 10.1007/s41060-016-0032-z |
| 25 | SAGI O , ROKACH L . Ensemble learning: a survey[J]. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery, 2018, 8 (5): e1249. |
| 26 |
YIN J N , LI N . Ensemble learning models with a Bayesian optimization algorithm for mineral prospectivity mapping[J]. ORE Geology Reviews, 2022, 145, 104916.
doi: 10.1016/j.oregeorev.2022.104916 |
| 27 | COLOMBO D , MAATHUIS M H . Order-independent constraint-based causal structure learning[J]. The Journal of Machine Learning Research, 2014, 15 (1): 3741- 3782. |
| 28 | YU Y, CHEN J, GAO T, et al. Dag-GNN: dag structure learning with graph neural networks[C]//Proc. of the International Conference on Machine Learning, 2019: 7154-7163. |
| 29 | ZHENG X, DAN C, ARAGAM B, et al. Learning sparse nonparametric dags[C]//Proc. of the International Conference on Articial Intelligence and Statistics, 2020: 3414-3425. |
| 30 | CHEN Y , ZHANG T B , WANG R J , et al. A Bayesian network structural learning algorithm for calculating the failure probabilities of complex engineering systems with limited data[J]. Journal of Intelligence and Fuzzy System, 2022, 42 (3): 1991- 2004. |
| [1] | Qian SU, Yuanfu ZHONG, Zhiqin CAO, Yingchao ZHANG. Target threat assessment model based on operational situation and improved CRITIC-TOPSIS [J]. Systems Engineering and Electronics, 2023, 45(8): 2343-2352. |
| [2] | Wenfei ZHAO, Yan WANG, Kenan TENG, Jian CHEN, Lu ZHOU. Target information processing model of air defence system for strategic location on the sea based on random service system [J]. Systems Engineering and Electronics, 2023, 45(11): 3565-3572. |
| [3] | Kun ZHANG, Zhenchong ZHANG, Zekun LIU, Ke LI, Peipei LIU. Multi-target dynamic threat assessment in mixed air combat based on FD-TODIM [J]. Systems Engineering and Electronics, 2023, 45(1): 148-154. |
| [4] | Xinyu XU, Lunjun WAN, Ping CHEN, Jiangbin DAI, Zhizhou GAO. Modeling of alert patrol airspace planning in defensive counterair interception operation [J]. Systems Engineering and Electronics, 2022, 44(5): 1589-1599. |
| [5] | Yingqi LU, Chengli FAN, Qiang FU, Xiaowen ZHU, Wei LI. Missile defense target threat assessment based on improved similarity measure and information entropy of IFRS [J]. Systems Engineering and Electronics, 2022, 44(4): 1230-1238. |
| [6] | Peng WANG, Zijing SUN, Fan ZHANG, Guosong XIAO. Reliability analysis model for phased-mission system considering probabilistic common cause failures [J]. Systems Engineering and Electronics, 2022, 44(12): 3887-3898. |
| [7] | Zheng XU, Guangzhong GONG, Yunhua LUO, Guangde LI. Application of improved spatial variant apodization algorithm through constrained optimization in sidelobe suppression [J]. Systems Engineering and Electronics, 2022, 44(11): 3298-3304. |
| [8] | Yanzhao LIU, Zhiqiu HUANG, Guohua SHEN, Jinyong WANG, Heng XU. Behavioral decision-making methods of autonomous vehicles based on decision tree and BN [J]. Systems Engineering and Electronics, 2022, 44(10): 3143-3154. |
| [9] | Bowen YU, Lin YU, Ming LYU, Jie ZHANG. Target threat assessment model based on M-ANFIS-PNN [J]. Systems Engineering and Electronics, 2022, 44(10): 3155-3163. |
| [10] | Chong JIN, Juan SUN, Yongjia WANG, Pushen CAI, Xin RONG. Threat comprehensive assessment for air defense targets based on intuitionistic fuzzy TOPSIS and variable weight VIKOR [J]. Systems Engineering and Electronics, 2022, 44(1): 172-180. |
| [11] | Yunke SUN, Zhigeng FANG, Ding CHEN. Multi-time threat assessment based on dynamic grey principal component analysis [J]. Systems Engineering and Electronics, 2021, 43(3): 740-746. |
| [12] | Guanglei MENG, Mingzhe ZHOU, Haiyin PIAO, Huimin ZHANG. Threat assessment method of dual-aircraft formation based on cooperative tactical recognition [J]. Systems Engineering and Electronics, 2020, 42(10): 2285-2293. |
| [13] | SUN Haiwen, XIE Xiaofang, SUN Tao, ZHANG Longjie. Threat assessment method of warships formation air defense based on DBN under the condition of small sample data missing [J]. Systems Engineering and Electronics, 2019, 41(6): 1300-1308. |
| [14] | SUN Qingpeng, LI Zhanwu, CHANG Yizhe. Multi-types airplane threat assessment based on combat power field [J]. Systems Engineering and Electronics, 2018, 40(9): 1993-1999. |
| [15] | XU Ximeng, YANG Rennong, FU Ying, ZHAO Yu. Target threat assessment in air combat based on ELM_AdaBoost strong predictor [J]. Systems Engineering and Electronics, 2018, 40(8): 1760-1768. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||