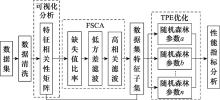
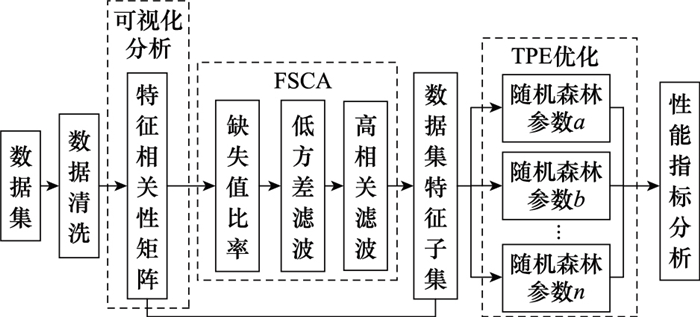
Systems Engineering and Electronics ›› 2021, Vol. 43 ›› Issue (7): 1954-1960.doi: 10.12305/j.issn.1001-506X.2021.07.27
• Communications and Networks • Previous Articles Next Articles
Intrusion detection based on feature selection and tree Parzen estimation
Zhigang JIN*, Tong WU
- School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
-
Received:2020-10-20Online:2021-06-30Published:2021-07-08 -
Contact:Zhigang JIN
CLC Number:
Cite this article
Zhigang JIN, Tong WU. Intrusion detection based on feature selection and tree Parzen estimation[J]. Systems Engineering and Electronics, 2021, 43(7): 1954-1960.
share this article
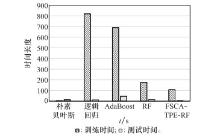
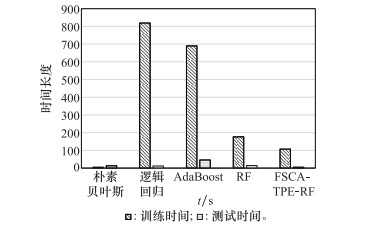
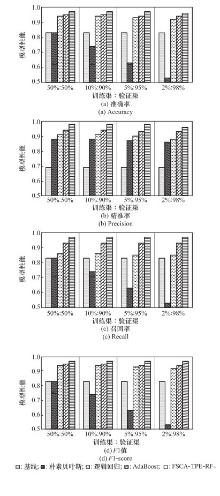
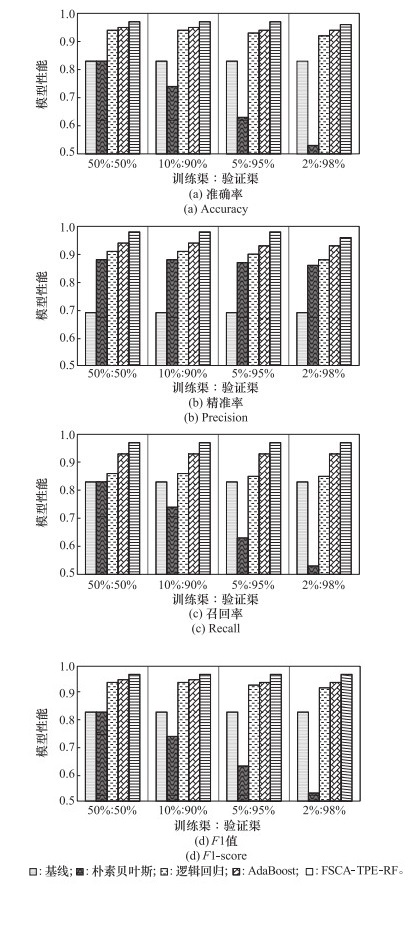
Table 2
Comparison of algorithm experiment results"
| 算法 | 评价指标 | |||
| A | P | R | F1 | |
| 基线 | 0.83 | 0.69 | 0.83 | 0.76 |
| 朴素贝叶斯 | 0.83 | 0.90 | 0.83 | 0.85 |
| 逻辑回归 | 0.94 | 0.91 | 0.87 | 0.89 |
| 自适应提升 | 0.95 | 0.94 | 0.93 | 0.94 |
| 随机森林 | 0.95 | 0.95 | 0.94 | 0.95 |
| 文献[ | 0.96 | 0.99 | 0.79 | - |
| 文献[ | 0.99 | 0.82 | 0.82 | 0.82 |
| 文献[ | 0.96 | 0.96 | 0.96 | 0.93 |
| FSCA-TPE-RF | 0.97 | 0.98 | 0.97 | 0.97 |
Table 2
| 1 | DISTIL N. Bad Bot Report 2020: bad bots strike back[EB/OL]. [2020-10-06]. https://www.imperva.com/resources/resource-library/reports/2020-bad-bot-report/. |
| 2 |
KHRAISAT A , GONDAL I , VAMPLEW P , et al. Survey of intrusion detection systems: techniques, datasets and challenges[J]. Cybersecurity, 2019, 2 (1): 1- 22.
doi: 10.1186/s42400-018-0018-3 |
| 3 | WANG Y , MENG W Z , LI W J , et al. Adaptive machine learning-based alarm reduction via edge computing for distributed intrusion detection systems[J]. Concurrency and Computation: Practice and Experience, 2019, 31 (19): e5101. |
| 4 |
ZHANG Q , YANG L T , CHEN Z , et al. A survey on deep learning for big data[J]. Information Fusion, 2018, 42, 146- 157.
doi: 10.1016/j.inffus.2017.10.006 |
| 5 | ATHMAJA S, HANUMANTHAPPA M, KAVITHA V. A survey of machine learning algorithms for big data analytics[C]//Proc. of the IEEE International Conference on Innovations in Information, Embedded and Communication Systems, 2017. |
| 6 |
LI H . Deep learning for natural language processing: advantages and challenges[J]. National Science Review, 2018, 5 (1): 24- 26.
doi: 10.1093/nsr/nwx110 |
| 7 | IBRAHIM M S, VAHDAT A, RANJBAR M, et al. Semi-supervised semantic image segmentation with self-correcting networks[C]//Proc. of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, 2020. |
| 8 | TAN M, PANG R, LE Q V. Efficientdet: scalable and efficient object detection[C]//Proc. of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, 2020. |
| 9 |
SHONE N , NGOC T N , PHAI V D , et al. A deep learning approach to network intrusion detection[J]. IEEE Trans.on Emerging Topics in Computational Intelligence, 2018, 2 (1): 41- 50.
doi: 10.1109/TETCI.2017.2772792 |
| 10 |
AN X S , LYU X , ZHOU X W , et al. Sample selected extreme learning machine based intrusion detection in fog computing and MEC[J]. Wireless Communications and Mobile Computing, 2018,
doi: 10.1155/2018/7472095 |
| 11 |
李元兵, 房鼎益, 吴晓南, 等. 基于神经网络的异常入侵检测系统[J]. 系统工程与电子技术, 2005, 27 (9): 1648- 1651.
doi: 10.3321/j.issn:1001-506X.2005.09.042 |
|
LI Y B , FANG D Y , WU X N , et al. Anomaly intrusion detection system based on neural network[J]. Systems Engineering and Electronics, 2005, 27 (9): 1648- 1651.
doi: 10.3321/j.issn:1001-506X.2005.09.042 |
|
| 12 | KIM J, KIM J, THU H L T, et al. Long short term memory recurrent neural network classifier for intrusion detection[C]//Proc. of the IEEE International Conference on Platform Technology and Service, 2016. |
| 13 | PUTCHALA M K. Deep learning approach for intrusion detection system (IDS) in the Internet of things (IoT) network using gated recurrent neural networks(GRU)[D]. Dayton: Wright State University, 2017. |
| 14 | 高妮, 高岭, 贺毅岳. 面向入侵检测系统的Deep Belief Nets模型[J]. 系统工程与电子技术, 2016, 38 (9): 2201- 2207. |
| GAO N , GAO L , HE Y Y . Deep belief nets model oriented to intrusion detection system[J]. Systems Engineering and Electronics, 2016, 38 (9): 2201- 2207. | |
| 15 | AYGUN R C, YAVUZ A G. Network anomaly detection with stochastically improved auto encoder based models[C]//Proc. of the IEEE 4th International Conference on Cyber Security and Cloud Computing, 2017. |
| 16 |
饶鲜, 杨绍全, 魏青, 等. 基于熵的入侵检测特征参数选择[J]. 系统工程与电子技术, 2006, 28 (4): 599- 601.
doi: 10.3321/j.issn:1001-506X.2006.04.029 |
|
RAO X , YANG S Q , WEI Q , et al. Selection intrusion detection parameters using entropy[J]. Systems Engineering and Electronics, 2006, 28 (4): 599- 601.
doi: 10.3321/j.issn:1001-506X.2006.04.029 |
|
| 17 |
HOOGE L , WAUTERS T , VOLCKAERT B , et al. Inter-dataset generalization strength of supervised machine learning methods for intrusion detection[J]. Journal of Information Security and Applications, 2020, 54, 102564.
doi: 10.1016/j.jisa.2020.102564 |
| 18 |
KIM J , KIM J , KIM H , et al. CNN-based network intrusion detection against denial-of-service attacks[J]. Electronics, 2020, 9 (6): 916.
doi: 10.3390/electronics9060916 |
| 19 | LIN P, YE K, XU C Z. Dynamic network anomaly detection system by using deep learning techniques[C]//Proc. of the International Conference on Cloud Computing, 2019. |
| 20 |
WANG W , SHENG Y Q , WANG J L , et al. HAST-IDS: learning hierarchical spatial-temporal features using deep neural networks to improve intrusion detection[J]. IEEE Access, 2018, 6, 1792- 1806.
doi: 10.1109/ACCESS.2017.2780250 |
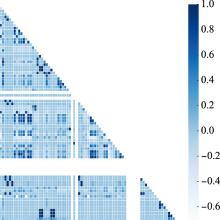
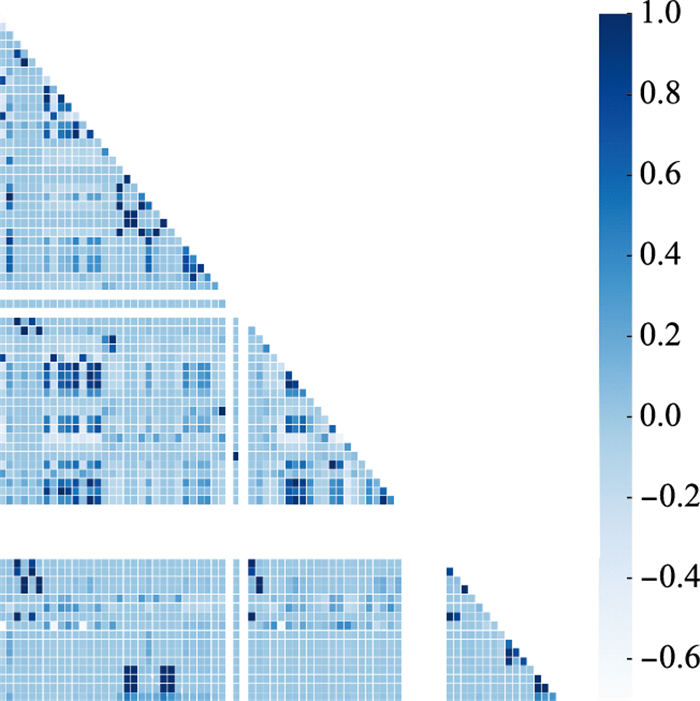
| 21 | GOOCH J W . Pearson correlation coefficient[M]. Atlanta: Encyclopedic Dictionary of Polymers, 2011. |
| 22 | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward generating a new intrusion detection dataset and intrusion traffic characterization[C]//Proc. of the International Confe-rence on Information Systems Security and Privacy, 2018. |
| 23 | Canadian Institute for Cybersecurity. A realistic cyber defense dataset (CSE-CIC-IDS2018)[EB/OL]. [2021-05-06]. https://registry.opendata.aws/cse-cic-ids2018/. |
| 24 | GHARIB A, SHARAFALDIN I, LASHKARI A H, et al. An evaluation framework for intrusion detection dataset[C]//Proc. of the IEEE International Conference on Information Scie-nce and Security, 2017. |
| 25 | CAI J , LUO J W , WANG S L , et al. Feature selection in machine learning: a new perspective[J]. Neurocomputing, 2018, 300 (26): 70- 79. |
| 26 | SAPUTRA F A, MASPUTRA M F, SYARIF I, et al. Botnet detection in network system through hybrid low variance filter, correlation filter and supervised mining process[C]//Proc. of the 13th International Conference on Digital Information Mana-gement, 2018. |
| 27 | COHEN-ADDAD V, KANADE V, MALLMANN T F, et al. Hierarchical clustering: objective functions and algorithms[C]//Proc. of the 29th Annual ACM-SIAM Symposium on Discrete Algorithms, 2018. |
| 28 |
LUJAN-MORENO G A , HOWARD P R , ROJAS O G , et al. Design of experiments and response surface methodology to tune machine learning hyper parameters with a random forest case-study[J]. Expert Systems with Applications, 2018, 109, 195- 205.
doi: 10.1016/j.eswa.2018.05.024 |
| 29 | PROBST P , WRIGHT M N , BOULESTEIX A L . Hyperparameters and tuning strategies for random forest[J]. Wiley Interdiplinary Reviews: Data Mining and Knowledge Discovery, 2019, 9 (3): e1301. |
| 30 | BERGSTRA J , BARDENET R , BENGIO Y , et al. Algorithms for hyper-parameter optimization[J]. Advances in Neural Information Processing Systems, 2011, 11, 2546- 2554. |
| [1] | Zexuan MA, Jin LI, Yanli LU, Chen CHEN. Network intrusion detection method based on WaveNet and BiGRU [J]. Systems Engineering and Electronics, 2022, 44(8): 2652-2660. |
| [2] | Bo LI, Jiahao ZHOU, Minmin LIU, Pinchao ZHU. Feature selection for welding defect assessment based on improved NSGA3 [J]. Systems Engineering and Electronics, 2022, 44(7): 2211-2218. |
| [3] | Jiacai YI, Bin LIU, Li YAO, Wentao ZHAO. Satellite cyber situational understanding based on knowledge reasoning [J]. Systems Engineering and Electronics, 2022, 44(5): 1562-1571. |
| [4] | Langcai CAO, Xiaochang LIN, Sixing SU. Unsupervised feature selection based on matrix factorization and adaptive graph [J]. Systems Engineering and Electronics, 2021, 43(8): 2197-2208. |
| [5] | Ruifeng LI, Aiqiang XU, Weichao SUN, Shuyou WANG. Recommendation method for avionics feature selection algorithm basedon meta-learning [J]. Systems Engineering and Electronics, 2021, 43(7): 2011-2020. |
| [6] | Yunhao SHI, Hua XU, Wanze ZHENG, Yinghui LIU. Few-shot modulation recognition method based on ensemble learning and feature dimension reduction [J]. Systems Engineering and Electronics, 2021, 43(4): 1099-1109. |
| [7] | Chunrong HE, Jiang ZHU. Security situation prediction method of GRU neural network [J]. Systems Engineering and Electronics, 2021, 43(1): 258-266. |
| [8] | Hongguang LI, Ying GUO, Ping SUI, Zisen QI, Linghua SU. Fine feature recognition of frequency hopping radio based on high dimensional feature selection [J]. Systems Engineering and Electronics, 2020, 42(2): 445-451. |
| [9] | ZHANG Yan, WANG Cunsong, LU Ningyun, JIANG Bin. Remaining useful life prediction for aeroengine based on thesimilarity of degradation characteristics [J]. Systems Engineering and Electronics, 2019, 41(6): 1414-1421. |
| [10] | LI Fangwei, LI Junyao, NIE Yifang, ZHU Jiang. Dynamic trust situation awareness mechanism based on multiagent system [J]. Systems Engineering and Electronics, 2017, 39(5): 1148-1153. |
| [11] | GAO Ni, GAO Ling, HE Yi-yue. Deep belief nets model oriented to intrusion detection system [J]. Systems Engineering and Electronics, 2016, 38(9): 2201-2207. |
| [12] | LI An-da, HE Zhen, HE Shu-guang. Critical to quality characteristics identification for complex products using GSA [J]. Systems Engineering and Electronics, 2015, 37(9): 2073-2079. |
| [13] | TONG Wei-ming, LIANG Jian-quan, LU Lei, JIN Xian-ji. Intrusion detection scheme based node trust value in WSNs [J]. Systems Engineering and Electronics, 2015, 37(7): 1644-1649. |
| [14] | QIAN Yu-wen, SONG Hua-ju, ZHAO Bang-xin, ZHANG Tong-fang,HAO Jin-song. Study on the detection algorithm of covert network behavior channel based on corrected entropy [J]. Journal of Systems Engineering and Electronics, 2013, 35(6): 1312-1217. |
| [15] | YAO Xu, WANG Xiao dan, ZHANG Yu xi, XING Yaqiong. Feature selection algorithm using PSO with adaptive mutation based t distribution [J]. Journal of Systems Engineering and Electronics, 2013, 35(6): 1335-1341. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||