Systems Engineering and Electronics ›› 2025, Vol. 47 ›› Issue (6): 1855-1866.doi: 10.12305/j.issn.1001-506X.2025.06.14
• Systems Engineering • Previous Articles Next Articles
Combat threat human-machine collaborative assessment framework based on IVSFS
Chongshuang HU, Jikai WANG, Minghao LI, Yajie DOU, Jiang JIANG
- College of Systems Engineering, National University of Defense Technology, Changsha 410073, China
-
Received:2023-05-22Online:2025-06-25Published:2025-07-09 -
Contact:Jiang JIANG
CLC Number:
Cite this article
Chongshuang HU, Jikai WANG, Minghao LI, Yajie DOU, Jiang JIANG. Combat threat human-machine collaborative assessment framework based on IVSFS[J]. Systems Engineering and Electronics, 2025, 47(6): 1855-1866.
share this article
Table 1
Sphereical fuzzy linguistic terms and their corresponding IVSFN"
| 语言术语 | 表述(缩写) | ( |
| 绝对更重要 | Absolutely more importance (AMI) | ([0.85, 0.95], [0.10, 0.15], [0.05, 0.15]) |
| 非常重要 | Very high importance (VHI) | ([0.75, 0.85], [0.15, 0.20], [0.15, 0.20]) |
| 很重要 | High importance (HI) | ([0.65, 0.75], [0.20, 0.25], [0.20, 0.25]) |
| 稍微更重要 | Slightly more importance (SMI) | ([0.55, 0.65], [0.25, 0.30], [0.25, 0.30]) |
| 相等重要 | Equally importance (EI) | ([0.50, 0.55], [0.45, 0.55], [0.30, 0.40]) |
| 稍微不重要 | Slightly low importance (SLI) | ([0.25, 0.30], [0.55, 0.65], [0.25, 0.30]) |
| 不重要 | Low importance (LI) | ([0.20, 0.25], [0.65, 0.75], [0.20, 0.25]) |
| 非常不重要 | Very low importance (VLI) | ([0.15, 0.20], [0.75, 0.85], [0.15, 0.20]) |
| 绝对不重要 | Absolutely low importance (ALI) | ([0.10, 0.15], [0.85, 0.95], [0.05, 0.15]) |
Table 2
Data of target objective attribute"
| U | T | 距离/m | 空袭高度/m | 速度/(km/h) | 航向角/(°) |
| u1 | t1 | [300, 320] | [700, 800] | [110, 150] | [6, 10] |
| t2 | [280, 320] | [820, 850] | [320, 350] | [12, 16] | |
| t3 | [150, 200] | [1 500, 1 700] | [350, 500] | [3, 6] | |
| t4 | [520, 550] | [1 200, 1 300] | [280, 350] | [12, 18] | |
| t5 | [800, 850] | [3 000, 3 500] | [250, 300] | [18, 25] | |
| u2 | t1 | [300, 320] | [720, 820] | [100, 130] | [6, 12] |
| t2 | [290, 320] | [800, 850] | [310 ,350] | [12, 16] | |
| t3 | [100, 160] | [1 500, 1 800] | [340, 500] | [3, 5] | |
| t4 | [510, 550] | [1 100, 1 300] | [300, 350] | [14, 20] | |
| t5 | [790, 850] | [3 000, 3 600] | [260, 300] | [16, 25] | |
| u3 | t1 | [310, 320] | [750, 820] | [100, 150] | [8, 10] |
| t2 | [290, 300] | [800, 850] | [310, 350] | [12, 16] | |
| t3 | [110, 180] | [1 600, 1 800] | [380, 500] | [3, 6] | |
| t4 | [510, 540] | [1 200, 1 400] | [300, 360] | [12, 18] | |
| t5 | [820, 860] | [2 800, 3 200] | [260, 300] | [16, 24] |
Table 3
IVSFS decision matrix of unmanned cluster"
| T | 距离/m | 空袭高度/m | 速度(km/h) | 航向角/(°) |
| t1 | < [0.28, 0.36], [0.52, 0.58], [0.04, 0.05]> | < [0.55, 0.57], [0.28, 0.31], [0.04, 0.05]> | < [0.21, 0.24], [0.86, 0.87], [0.04, 0.05]> | < [0.15, 0.27], [0.40, 0.56], [0.03, 0.06]> |
| t2 | < [0.28, 0.36], [0.49, 0.57], [0.04, 0.06]> | < [0.53, 0.55], [0.36, 0.39], [0.05, 0.06]> | < [0.55, 0.57], [0.59, 0.60], [0.04, 0.05]> | < [0.11, 0.17], [0.70, 0.71], [0.04, 0.06]> |
| t3 | < [0.53, 0.58], [0.05, 0.26], [0.04, 0.06]> | < [0.25, 0.27], [0.66, 0.68], [0.04, 0.07]> | < [0.78, 0.81], [0.52, 0.56], [0.04, 0.05]> | < [0.46, 0.66], [0.17, 0.80], [0.05, 0.06]> |
| t4 | < [0.16, 0.21], [0.73, 0.75], [0.05, 0.07]> | < [0.34, 0.35], [0.54, 0.58], [0.05, 0.07]> | < [0.56, 0.57], [0.61, 0.64], [0.04, 0.06]> | < [0.09, 0.13], [0.70, 0.78], [0.05, 0.07]> |
| t5 | < [0.10, 0.14], [0.82, 0.84], [0.05, 0.06]> | < [0.13, 0.13], [0.83, 0.83], [0.04, 0.06]> | < [0.47, 0.49], [0.66, 0.68], [0.04, 0.05]> | < [0.07, 0.11], [0.78, 0.80], [0.06, 0.06]> |
Table 4
Expert IVSF decision matrix"
| E | T | 类型 | 侦察 | 干扰 | 打击 | 防御 |
| e1 | t1 | SMI | SMI | HI | SLI | SMI |
| t2 | SLI | VHI | VLI | ALI | SML | |
| t3 | VHI | VLI | SLI | AMI | EI | |
| t4 | EI | SMI | EI | SMI | SLI | |
| t5 | HI | LI | LI | HI | VHI | |
| e2 | t1 | HI | SMI | SMI | HI | EI |
| t2 | SMI | AMI | EI | VLI | LI | |
| t3 | VHI | VLI | VLI | VHI | AMI | |
| t4 | SMI | EI | HI | EI | SMI | |
| t5 | VHI | EI | HI | EI | EI | |
| e3 | t1 | SMI | EI | HI | EI | EI |
| t2 | EI | VHI | HI | VLI | LI | |
| t3 | VHI | LI | VLI | VHI | VHI | |
| t4 | SMI | SMI | HI | EI | SLI | |
| t5 | HI | VHI | VHI | SMI | EI |
Table 5
Three distance types for initial decision matrix"
| e | t1 | t2 | t3 | t4 | t5 | 距离类型 |
| e1 | 0.06 | 0.12 | 0.07 | 0.07 | 0.15 | DGWMDik |
| e2 | 0.05 | 0.06 | 0.03 | 0.05 | 0.07 | |
| e3 | 0.03 | 0.07 | 0.02 | 0.04 | 0.08 | |
| e1 | 0.07 | 0.14 | 0.07 | 0.09 | 0.17 | DGBDik |
| e2 | 0.03 | 0.09 | 0.04 | 0.03 | 0.14 | |
| e3 | 0.08 | 0.10 | 0.05 | 0.06 | 0.08 | |
| e1 | 0.05 | 0.06 | 0.04 | 0.03 | 0.08 | DGWDik |
| e2 | 0.08 | 0.11 | 0.06 | 0.09 | 0.11 | |
| e3 | 0.04 | 0.11 | 0.05 | 0.06 | 0.17 |
Table 7
Group weight mean decision matrix based on the revised expert weight"
| T | 类型 | 侦察 | 干扰 | 打击 | 防御 |
| t1 | < [0.59, 0.69], [0.23, 0.28], [0.05, 0.08]> | < [0.53, 0.62], [0.31, 0.37], [0.07, 0.11]> | < [0.62, 0.72], [0.22, 0.27], [0.05, 0.07]> | < [0.52, 0.6], [0.36, 0.44], [0.06, 0.10]> | < [0.52, 0.58], [0.38, 0.46], [0.08, 0.14]> |
| t2 | < [0.47, 0.54], [0.39, 0.47], [0.07, 0.12]> | < [0.79, 0.9], [0.13, 0.18], [0.01, 0.03]> | < [0.51, 0.59], [0.39, 0.47], [0.05, 0.10]> | < [0.14, 0.19], [0.78, 0.88], [0.02, 0.04]> | < [0.42, 0.50], [0.46, 0.54], [0.04, 0.07]> |
| t3 | < [0.75, 0.85], [0.15, 0.20], [0.02, 0.04]> | < [0.17, 0.22], [0.71, 0.81], [0.03, 0.05]> | < [0.19, 0.23], [0.68, 0.78], [0.03, 0.06]> | < [0.79, 0.89], [0.13, 0.18], [0.02, 0.03]> | < [0.75, 0.86], [0.18, 0.24], [0.03, 0.05]> |
| t4 | < [0.54, 0.62], [0.30, 0.36], [0.07, 0.11]> | < [0.53, 0.62], [0.31, 0.37], [0.07, 0.11]> | < [0.61, 0.71], [0.25, 0.32], [0.05, 0.08]> | < [0.52, 0.58], [0.38, 0.46], [0.08, 0.14]> | < [0.39, 0.47], [0.42, 0.50], [0.06, 0.09]> |
| t5 | < [0.69, 0.79], [0.18, 0.23], [0.03, 0.05]> | < [0.58, 0.67], [0.34, 0.42], [0.05, 0.08]> | < [0.63, 0.73], [0.26, 0.32], [0.03, 0.06]> | < [0.57, 0.66], [0.29, 0.35], [0.06, 0.10]> | < [0.60, 0.69], [0.32, 0.41], [0.06, 0.11]> |
Table 23
Evaluation result of unmanned swarms based on TOPSIS, GRA, GRA-TOPSIS and GRA-CPT-TOPSIS"
| 指标 | t1 | t2 | t3 | t4 | t5 | 排序 |
| UDCR | 0.46 | 0.63 | 0.83 | 0.42 | 0.17 | t3>t2>t1>t4>t5 |
| UGCR | 0.48 | 0.55 | 0.65 | 0.45 | 0.33 | t3>t2>t1>t4>t5 |
| UCCR | 0.48 | 0.57 | 0.70 | 0.44 | 0.29 | t3>t2>t1>t4>t5 |
| upij | -0.78 | -0.62 | -0.21 | -0.95 | -1.32 | t3>t2>t1>t4>t5 |
Table 26
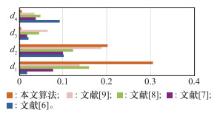
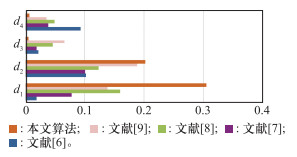
Target threat ranking and differentiation of different methods"
| 方法 | 综合威胁度R | d1 | d2 | d3 | d4 |
| 文献[ | t3(1.00)>t1(0.98)>t2(0.88)>t5(0.86)>t4(0.78) | 0.02 | 0.10 | 0.02 | 0.09 |
| 文献[ | t3(0.64)>t1(0.59)>t2(0.53)>t5(0.52)>t4(0.50) | 0.08 | 0.10 | 0.02 | 0.04 |
| 文献[ | t3(0.87)>t1(0.73)>t2(0.64)>t5(0.61)>t4(0.58) | 0.16 | 0.12 | 0.05 | 0.05 |
| 文献[ | t3(0.43)>t1(0.37)>t2(0.30)>t5(0.28)>t4(0.27) | 0.14 | 0.19 | 0.07 | 0.04 |
| 本文算法 | t3(-0.49)>t1(-0.64)>t2(-0.77)>t5(-0.77)>t4(-0.78) | 0.31 | 0.20 | 0.01 | 0.01 |
| 1 | MICHAEL M. Effective decision-making employing human-machine teaming[R]. Newport: Naval War College, 2022. |
| 2 | KERBUSCH P, KEIJSER B, SMIT S. Roles of AI and simulation for military decision making[C]//Proc. of the STO Meeting Proceedings MP-IST-160, 2018. |
| 3 |
JOHNSON J . Automating the OODA loop in the age of intelligent machines: reaffirming the role of humans in command-and-control decision-making in the digital age[J]. Defence Studies, 2023, 23 (1): 43- 67.
doi: 10.1080/14702436.2022.2102486 |
| 4 | LLINAS J, HALL D L. An introduction to multi-sensor data fusion[C]//Proc. of the IEEE International Symposium on Circuits and Systems, 1998: 537-540. |
| 5 | LI S Y, WU Q X, CHEN M, et al. Air combat situation assessment of multiple UCAVs with incomplete information[C]//Proc. of the Chinese Intelligent Systems Conference, 2021: 18- 26. |
| 6 |
张浩为, 谢军伟, 葛佳昂, 等. 改进TOPSIS的多态融合直觉模糊威胁评估[J]. 系统工程与电子技术, 2018, 40 (10): 2263- 2269.
doi: 10.3969/j.issn.1001-506X.2018.10.16 |
|
ZHANG H W , XIE J W , GE J A , et al. Intuitionistic fuzzy set threat assessment based on improved TOPSIS and multiple times fusion[J]. Systems Engineering and Electronics, 2018, 40 (10): 2263- 2269.
doi: 10.3969/j.issn.1001-506X.2018.10.16 |
|
| 7 | 卢盈齐, 范成礼, 付强, 等. 基于改进IFRS相似度和信息熵的反导作战目标威胁评估[J]. 系统工程与电子技术, 2022, 44 (4): 1230- 1238. |
| LU Y Q , FAN C L , FU Q , et al. Missile defense target threat assessment based on improved similarity measure and information entropy of IFRS[J]. Systems Engineering and Electronics, 2022, 44 (4): 1230- 1238. | |
| 8 |
KUN Z , WEIREN K , PEIPEI L , et al. Assessment and sequencing of air target threat based on intuitionistic fuzzy entropy and dynamic VIKOR[J]. Journal of Systems Engineering and Electronics, 2018, 29 (2): 305- 310.
doi: 10.21629/JSEE.2018.02.11 |
| 9 | 靳崇, 孙娟, 王永佳, 等. 基于直觉模糊TOPSIS和变权VIKOR的防空目标威胁综合评估[J]. 系统工程与电子技术, 2022, 44 (1): 172- 180. |
| JIN C , SUN J , WANG Y J , et al. Threat comprehensive assessment for air defense targets based on intuitionistic fuzzy TOPSIS and variable weight VIKOR[J]. Systems Engineering and Electronics, 2022, 44 (1): 172- 180. | |
| 10 | 陈刚, 姚丽亚, 王国新, 等. 面向鲁棒决策的战场态势评估人机共识形成方法[J]. 兵工学报, 2022, 43 (11): 2953- 2964. |
| CHEN G , YAO L Y , WANG G X , et al. A human-machine consensus formation method for robust decision making in battlefield situation assessment[J]. Acta Armamentarii, 2022, 43 (11): 2953- 2964. | |
| 11 |
ZADEH L A . Fuzzy sets[J]. Information and Control, 1965, 8 (3): 338- 353.
doi: 10.1016/S0019-9958(65)90241-X |
| 12 |
ATANASSOV K T . Intuitionistic fuzzy sets[J]. Fuzzy Sets and Systems, 1986, 20 (1): 87- 96.
doi: 10.1016/S0165-0114(86)80034-3 |
| 13 |
YAGER R R , ABBASOV A M . Pythagorean membership grades, complex numbers, and decision making[J]. International Journal of Intelligent Systems, 2013, 28 (5): 436- 452.
doi: 10.1002/int.21584 |
| 14 | CUONG B C . Picture fuzzy sets[J]. Journal of Computer Science and Cybernetics, 2014, 30 (4): 409. |
| 15 | ASHRAF S , ABDULLAH S , MAHMOOD T , et al. Spherical fuzzy sets and their applications in multi-attribute decision making problems[J]. Journal of Intelligent & Fuzzy Systems, 2019, 36 (3): 2829- 2844. |
| 16 |
BARUKAB O , ABDULLAH S , ASHRAF S , et al. A new approach to fuzzy TOPSIS method based on entropy measure under spherical fuzzy information[J]. Entropy, 2019, 21 (12): 1231.
doi: 10.3390/e21121231 |
| 17 | KUTLU GUNDOGDU F , KAHRAMAN C . Spherical fuzzy sets and spherical fuzzy TOPSIS method[J]. Journal of Intelligent & Fuzzy Systems, 2019, 36 (1): 337- 352. |
| 18 |
AKRAM M , SALEEM D , AL-HAWARY T . Spherical fuzzy graphs with application to decision-making[J]. Mathematical and Computational Applications, 2020, 25 (1): 8.
doi: 10.3390/mca25010008 |
| 19 |
MATHEW M , CHAKRABORTTY R K , RYAN M J . A novel approach integrating AHP and TOPSIS under spherical fuzzy sets for advanced manufacturing system selection[J]. Engineering Applications of Artificial Intelligence, 2020, 96, 103988.
doi: 10.1016/j.engappai.2020.103988 |
| 20 |
ZHANG H Y , WEI G W , CHEN X D . SF-GRA method based on cumulative prospect theory for multiple attribute group decision making and its application to emergency supplies supplier selection[J]. Engineering Applications of Artificial Intelligence, 2022, 110, 104679.
doi: 10.1016/j.engappai.2022.104679 |
| 21 |
RAHNAMAY B S , JAFARZADEH G S , DEVECI M , et al. Logistic autonomous vehicles assessment using decision support model under spherical fuzzy set integrated Choquet integral approach[J]. Expert Systems with Applications, 2023, 214, 119205.
doi: 10.1016/j.eswa.2022.119205 |
| 22 |
HASELI G , JAFARZADEH G S . Extended base-criterion method based on the spherical fuzzy sets to evaluate waste management[J]. Soft Computing, 2022, 26 (19): 9979- 9992.
doi: 10.1007/s00500-022-07366-4 |
| 23 |
ZADEH L A . The concept of a linguistic variable and its application to approximate reasoning[J]. Information Sciences, 1975, 8 (3): 199- 249.
doi: 10.1016/0020-0255(75)90036-5 |
| 24 | ATANASSOV K T. On interval valued intuitionistic fuzzy sets[M] //Cham: Springer International Publishing, 2020. |
| 25 | GARG H . A novel accuracy function under interval-valued Pythagorean fuzzy environment for solving multicriteria decision making problem[J]. Journal of Intelligent & Fuzzy Systems, 2016, 31 (1): 529- 540. |
| 26 |
KHALIL A M , LI S G , GARG H , et al. New operations on interval-valued picture fuzzy set, interval-valued picture fuzzy soft set and their applications[J]. IEEE Access, 2019, 7, 51236- 51253.
doi: 10.1109/ACCESS.2019.2910844 |
| 27 |
KUTLU GUNDOGDU F , KAHRAMAN C . A novel fuzzy TOPSIS method using emerging interval-valued spherical fuzzy sets[J]. Engineering Applications of Artificial Intelligence, 2019, 85, 307- 323.
doi: 10.1016/j.engappai.2019.06.003 |
| 28 |
韩博文, 姚佩阳, 钟赟, 等. 基于QABC-IFMADM算法的有人/无人机编队作战威胁评估[J]. 电子学报, 2018, 46 (7): 1584- 1592.
doi: 10.3969/j.issn.0372-2112.2018.07.007 |
|
HAN B W , YAO P Y , ZHONG Y , et al. Threat assessment of manned/unmanned aerial vehicle formation based on QABC-IFMADM algorithm[J]. Acta Electronica Sinica, 2018, 46 (7): 1584- 1592.
doi: 10.3969/j.issn.0372-2112.2018.07.007 |
|
| 29 |
TVERSKY A , KAHNEMAN D . Advances in prospect theory: cumulative representation of uncertainty[J]. Journal of Risk and Uncertainty, 1992, 5 (4): 297- 323.
doi: 10.1007/BF00122574 |
| 30 |
LIU J C , XU F Q , LIN S S . Site selection of photovoltaic power plants in a value chain based on grey cumulative prospect theory for sustainability: a case study in Northwest China[J]. Journal of Cleaner Production, 2017, 148, 386- 397.
doi: 10.1016/j.jclepro.2017.02.012 |
| [1] | Zidong WANG, Xiaoguang GAO, Xiaohan LIU. Target threat assessment based on ensemble Bayesian network with Stacking strategy [J]. Systems Engineering and Electronics, 2024, 46(2): 586-598. |
| [2] | Qian SU, Yuanfu ZHONG, Zhiqin CAO, Yingchao ZHANG. Target threat assessment model based on operational situation and improved CRITIC-TOPSIS [J]. Systems Engineering and Electronics, 2023, 45(8): 2343-2352. |
| [3] | Wenfei ZHAO, Yan WANG, Kenan TENG, Jian CHEN, Lu ZHOU. Target information processing model of air defence system for strategic location on the sea based on random service system [J]. Systems Engineering and Electronics, 2023, 45(11): 3565-3572. |
| [4] | Kun ZHANG, Zhenchong ZHANG, Zekun LIU, Ke LI, Peipei LIU. Multi-target dynamic threat assessment in mixed air combat based on FD-TODIM [J]. Systems Engineering and Electronics, 2023, 45(1): 148-154. |
| [5] | Xinyu XU, Lunjun WAN, Ping CHEN, Jiangbin DAI, Zhizhou GAO. Modeling of alert patrol airspace planning in defensive counterair interception operation [J]. Systems Engineering and Electronics, 2022, 44(5): 1589-1599. |
| [6] | Yingqi LU, Chengli FAN, Qiang FU, Xiaowen ZHU, Wei LI. Missile defense target threat assessment based on improved similarity measure and information entropy of IFRS [J]. Systems Engineering and Electronics, 2022, 44(4): 1230-1238. |
| [7] | Bowen YU, Lin YU, Ming LYU, Jie ZHANG. Target threat assessment model based on M-ANFIS-PNN [J]. Systems Engineering and Electronics, 2022, 44(10): 3155-3163. |
| [8] | Chong JIN, Juan SUN, Yongjia WANG, Pushen CAI, Xin RONG. Threat comprehensive assessment for air defense targets based on intuitionistic fuzzy TOPSIS and variable weight VIKOR [J]. Systems Engineering and Electronics, 2022, 44(1): 172-180. |
| [9] | Yunke SUN, Zhigeng FANG, Ding CHEN. Multi-time threat assessment based on dynamic grey principal component analysis [J]. Systems Engineering and Electronics, 2021, 43(3): 740-746. |
| [10] | Guanglei MENG, Mingzhe ZHOU, Haiyin PIAO, Huimin ZHANG. Threat assessment method of dual-aircraft formation based on cooperative tactical recognition [J]. Systems Engineering and Electronics, 2020, 42(10): 2285-2293. |
| [11] | SUN Haiwen, XIE Xiaofang, SUN Tao, ZHANG Longjie. Threat assessment method of warships formation air defense based on DBN under the condition of small sample data missing [J]. Systems Engineering and Electronics, 2019, 41(6): 1300-1308. |
| [12] | SUN Qingpeng, LI Zhanwu, CHANG Yizhe. Multi-types airplane threat assessment based on combat power field [J]. Systems Engineering and Electronics, 2018, 40(9): 1993-1999. |
| [13] | XU Ximeng, YANG Rennong, FU Ying, ZHAO Yu. Target threat assessment in air combat based on ELM_AdaBoost strong predictor [J]. Systems Engineering and Electronics, 2018, 40(8): 1760-1768. |
| [14] | ZHANG Ying, WANG Hongwei, CHEN You. Combined emitter threat assessment based on ICWM-RCM [J]. Systems Engineering and Electronics, 2018, 40(3): 557-562. |
| [15] | OUYANG Zhihong, XUE Lei, DING Feng. Jamming target assignment method of regional electronic air defense against electrooptical precision guided weapon#br# [J]. Systems Engineering and Electronics, 2018, 40(12): 2621-2628. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||