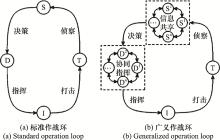
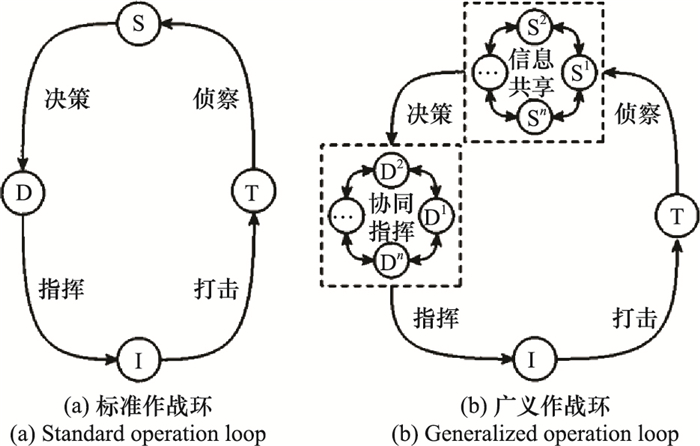
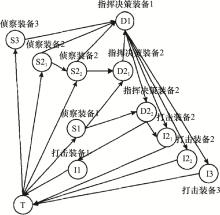
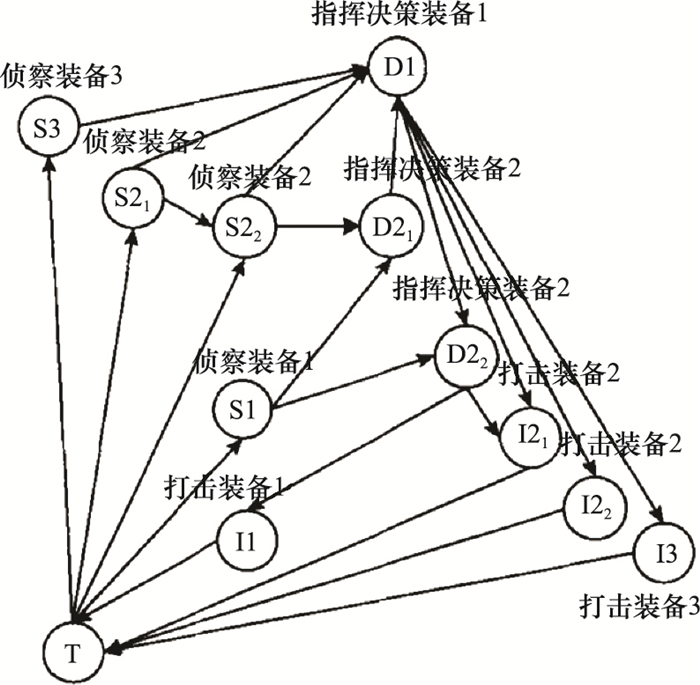
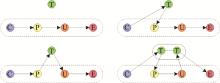
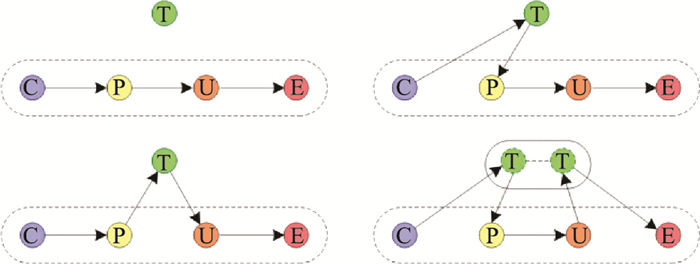
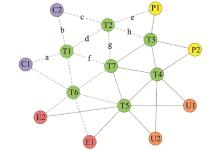
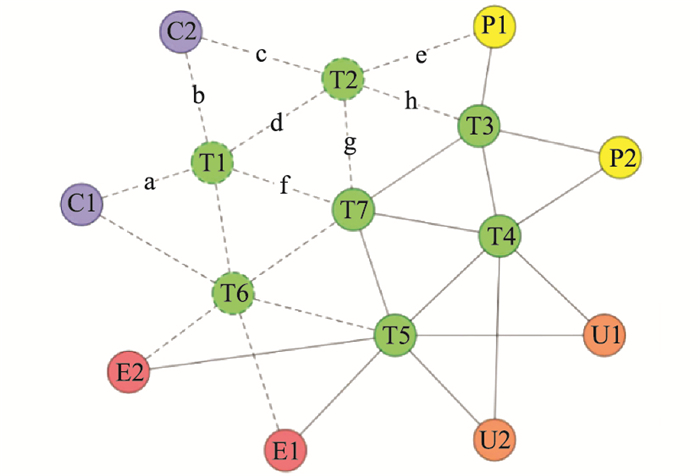
Systems Engineering and Electronics ›› 2022, Vol. 44 ›› Issue (8): 2515-2521.doi: 10.12305/j.issn.1001-506X.2022.08.16
• Systems Engineering • Previous Articles Next Articles
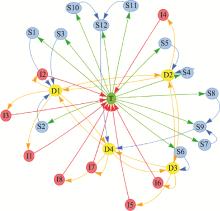
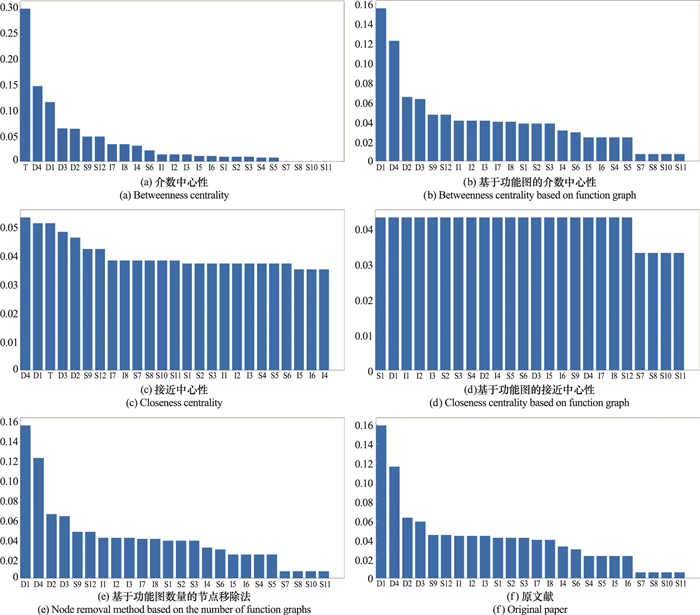
Analysis of key nodes in combat system based on function graph
Jianxing GONG1,2, Lei ZHU1,*, Huabing WANG2, Peiyuan DING1, Chengzhao LU1
- 1. College of Intelligence Science and Engineering, National University of Defense Technology, Changsha 410073, China
2. State Key Laboratory of Complex Electromagnetic Environment Effect on Electronics and Information System, Luoyang 471003, China
-
Received:2021-06-04Online:2022-08-01Published:2022-08-24 -
Contact:Lei ZHU
CLC Number:
Cite this article
Jianxing GONG, Lei ZHU, Huabing WANG, Peiyuan DING, Chengzhao LU. Analysis of key nodes in combat system based on function graph[J]. Systems Engineering and Electronics, 2022, 44(8): 2515-2521.
share this article
| 1 |
李茂林, 龙建国, 张德群. 基于复杂网络理论的作战体系节点重要性分析[J]. 指挥控制与仿真, 2010, 32 (3): 15- 17.
doi: 10.3969/j.issn.1673-3819.2010.03.005 |
|
LI M L , LONG J G , ZHANG D Q . Analysis of node's importance of combat system based on theory of complex networks[J]. Command Control & Simulation, 2010, 32 (3): 15- 17.
doi: 10.3969/j.issn.1673-3819.2010.03.005 |
|
| 2 | 姜志鹏, 张多林, 王乐, 等. 多维约束下指挥网络节点重要度的评估方法[J]. 解放军理工大学学报(自然科学版), 2015, (3): 294- 298. |
| JIANG Z P , ZHANG D L , WANG L , et al. Evaluation method for node importance of command network with multiple constraints[J]. Journal of PLA University of Science and Technology (Natural Science Edition), 2015, (3): 294- 298. | |
| 3 | 孙成雨, 申卯兴, 王宇峰, 等. 作战体系加权网络节点重要度评估[J]. 装甲兵工程学院学报, 2016, 30 (5): 95- 99. |
| SUN C Y , SHEN M X , WANG Y F , et al. Node importance evaluation for weighted combat SoS network[J]. Journal of Academy of Armored Force Engineering, 2016, 30 (5): 95- 99. | |
| 4 | LYU L Y, CHEN D B, REN X L, et al. Vital nodes identification in complex networks[EB/OL]. [2021-04-20]. https://arXiv.org/abs/1607.01134. |
| 5 |
BORGATTI S P , EVERETT M G . A graph-theoretic perspective on centrality[J]. Social Networks, 2006, 28 (4): 466- 484.
doi: 10.1016/j.socnet.2005.11.005 |
| 6 | CARES J R . An information age combat model[J]. Paper for ICCRTS, 2014, 27 (404): 103- 105. |
| 7 |
谭跃进, 张小可, 杨克巍. 武器装备体系网络化描述与建模方法[J]. 系统管理学报, 2012, 21 (6): 781- 786.
doi: 10.3969/j.issn.1005-2542.2012.06.009 |
|
TAN Y J , ZHANG X K , YANG K W . Research on networked description and modeling methods of armament system-of-systems[J]. Journal of Systems & Management, 2012, 21 (6): 781- 786.
doi: 10.3969/j.issn.1005-2542.2012.06.009 |
|
| 8 | 李国栋, 王鹏. 基于作战环的作战体系节点重要性评价方法[J]. 火力与指挥控制, 2019, 44 (8): 7- 11. |
| LI G D , WANG P . Node importance evaluation for operation system of systems based on operation loop[J]. Fire Control & Command Control, 2019, 44 (8): 7- 11. | |
| 9 | 赵丹玲, 谭跃进, 李际超, 等. 基于作战环的武器装备体系贡献度评估[J]. 系统工程与电子技术, 2017, 39 (10): 2239- 2247. |
| ZHAO D L , TAN Y J , LI J C , et al. Armament system of systems contribution evaluation based on operation loop[J]. Systems Engineering and Electronics, 2017, 39 (10): 2239- 2247. | |
| 10 | 梁家林, 熊伟. 基于作战环的武器装备体系能力评估方法[J]. 系统工程与电子技术, 2019, 41 (8): 1810- 1819. |
| LIANG J L , XIONG W . Capabilities assessment of the wea-ponry system based on combat ring[J]. Systems Engineering and Electronics, 2019, 41 (8): 1810- 1819. | |
| 11 | 刘鹏, 赵丹玲, 谭跃进, 等. 面向多任务的武器装备体系贡献度评估方法[J]. 系统工程与电子技术, 2019, 41 (8): 1763- 1770. |
| LIU P , ZHAO D L , TAN Y J , et al. Multi-task oriented contribution evaluation method of weapon equipment system of systems[J]. Systems Engineering and Electronics, 2019, 41 (8): 1763- 1770. | |
| 12 | 任晓龙, 吕琳媛. 网络重要节点排序方法综述[J]. 科学通报, 2014, 59 (13): 1175- 1197. |
| REN X L , LYU L Y . Review of ranking nodes in complex networks[J]. Chinese Science Bulletin Journal, 2014, 59 (13): 1175- 1197. | |
| 13 | 石福丽. 基于超网络的军事通信网络建模、分析与重构方法研究[D]. 长沙: 国防科学技术大学, 2013. |
| SHI F L. Research on supernetwork based modeling and analysis for military communication network reconflguration[D]. Changsha: National University of Defense Technology, 2013. | |
| 14 |
BONACICH P F . Factoring and weighting approaches to status scores and clique identification[J]. Journal of Mathematical Sociology, 1972, 2 (1): 113- 120.
doi: 10.1080/0022250X.1972.9989806 |
| 15 |
BRANDES U . A faster algorithm for betweenness centrality[J]. Journal of Mathematical Sociology, 2001, 25 (2): 163- 177.
doi: 10.1080/0022250X.2001.9990249 |
| 16 |
BRIN S , PAGE L . The anatomy of a large-scale hypertextual Web search engine[J]. Computer Networks and ISDN Systems, 1998, 30 (1-7): 107- 117.
doi: 10.1016/S0169-7552(98)00110-X |
| 17 | LI P X , REN Y Q , XI Y M . An importance measure of actors (set) within a network[J]. Systems Engineering, 2004, 22 (4): 13- 20. |
| 18 | WANG Y L , XU J , XI Y M . The core and coritivity of a system Relations betweeu asystew and its Complemcnt[J]. Journal of System Engineering and Electronics, 1993, 4 (2): 28- 34. |
| 19 |
包学才, 戴伏生, 韩卫占. 基于拓扑的不相交路径抗毁性评估方法[J]. 系统工程与电子技术, 2012, 34 (1): 168- 174.
doi: 10.3969/j.issn.1001-506X.2012.01.31 |
|
BAO X C , DAI F S , HAN W Z . Evaluation method of network invulnerability based on disjoint paths in topology[J]. Systems Engineering and Electronics, 2012, 34 (1): 168- 174.
doi: 10.3969/j.issn.1001-506X.2012.01.31 |
|
| 20 |
DANGALCHEV C . Residual closeness in networks[J]. Physica a Statistical Mechanics and its Application, 2006, 365 (2): 556- 564.
doi: 10.1016/j.physa.2005.12.020 |
| 21 | CHEN Y , HU A Q , HU X . Evaluation method for node importance in communication networks[J]. Journal of China Institute of Communications, 2004, 25 (8): 129- 134. |
| 22 |
RESTREPO J G , OTT E , HUNT B R . Characterizing the dynamical importance of network nodes and links[J]. Physical Review Letters, 2006, 97 (9): 094102.
doi: 10.1103/PhysRevLett.97.094102 |
| 23 | TAN Y J , WU J , DENG H Z . Evaluation method for node importance based on node contraction in complex networks[J]. Systems Engineering-Theory & Practice, 2006, 11 (11): 79- 83. |
| 24 |
KATZ L . A new status index derived from sociometric analysis[J]. Psychometrika, 1953, 18 (1): 39- 43.
doi: 10.1007/BF02289026 |
| 25 |
HOLME P , SARAMÄKI J . Temporal networks[J]. Physics Reports, 2012, 519 (3): 97- 125.
doi: 10.1016/j.physrep.2012.03.001 |
| [1] | Shunqi HUAN, Zhemei FAN, Jianbo WANG. System-of-systems effectiveness evaluation method based on functional dependency network [J]. Systems Engineering and Electronics, 2022, 44(7): 2191-2200. |
| [2] | Tongliang LU, Wenhao CHEN, Bingfeng GE, Qiling DENG. Multi-layer network modeling for combat system-of-systems under information support [J]. Systems Engineering and Electronics, 2022, 44(2): 520-528. |
| [3] | Meigen HUANG, Weiping WANG, Tao WANG, Xiaobo LI, Hua HE, Song YANG. EC2-based architecture design method of cloud-flow C2 for unmanned combat SoS [J]. Systems Engineering and Electronics, 2022, 44(11): 3413-3422. |
| [4] | Yantao WANG, Zheng YANG. Propagation and control improvement of flight operation risk network [J]. Systems Engineering and Electronics, 2021, 43(9): 2544-2552. |
| [5] | Guangxun ZENG, Guanghong GONG, Ni LI. Combat system-of-systems simulation scenario generation approach based on semantic matching [J]. Systems Engineering and Electronics, 2021, 43(8): 2154-2162. |
| [6] | Yue GAO, Le RU, Wensheng CHI, Qing ZHOU. Task meta-model modeling of air combat systembased on system architecture design [J]. Systems Engineering and Electronics, 2021, 43(11): 3229-3238. |
| [7] | Guixiang FANG, Yuejin TAN, Mu ZHANG, Xiaodong BU, Jun ZHANG. Evaluation of relative contribution rate of missile weapon system-of-systems based on combat ring [J]. Systems Engineering and Electronics, 2020, 42(8): 1734-1739. |
| [8] | NIU Liqiang, XIE Yongjun, ZHANG Chungang, WU Dongwei. Detection simulation of AEGIS combat system for ballistic missile in electronic warfare environment [J]. Systems Engineering and Electronics, 2019, 41(6): 1195-1201. |
| [9] | ZHANG Xianchao, MA Yahui. Capability model of combat system of systems and measurement method of armament contribution to combat system of systems [J]. Systems Engineering and Electronics, 2019, 41(4): 843-849. |
| [10] | LI Jiawei, WU Minggong, WEN Xiangxi, LIU Fei. Identifying key nodes and edges of complex networks based on the minimum connected dominating set [J]. Systems Engineering and Electronics, 2019, 41(11): 2541-2549. |
| [11] | LUO Kai, ZHANG Ming-zhi, WU Xi. Key nodes analysis model for space information temporal network based on operation loop [J]. Systems Engineering and Electronics, 2016, 38(7): 1572-1576. |
| [12] | YAN Ji, LI Xiang-min, LIU Li-jia, LIU Bo. Combat network synchronization of air fleet formation [J]. Systems Engineering and Electronics, 2014, 36(8): 1566-1572. |
| [13] | XIONG Song, ZHOU Jun, HU Wei-jun. Dynamic balancing combat system simulation based on extended HLA [J]. Systems Engineering and Electronics, 2014, 36(4): 789-794. |
| [14] | BAO Xuecai, DAI Fusheng, HAN Weizhan. Evaluation method of network invulnerability based on disjoint paths in topology [J]. Journal of Systems Engineering and Electronics, 2012, 34(1): 168-174. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||