Systems Engineering and Electronics ›› 2025, Vol. 47 ›› Issue (7): 2127-2135.doi: 10.12305/j.issn.1001-506X.2025.07.06
• Electronic Technology • Previous Articles
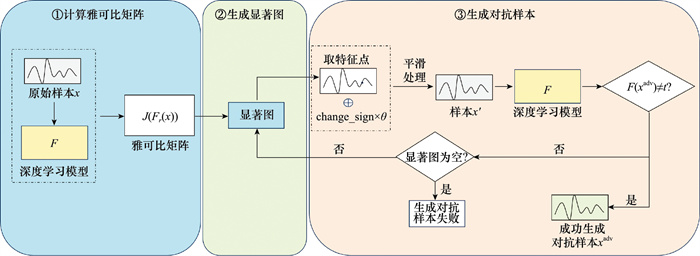
Electromagnetic signal no-targeted smooth adversarial attack method based on Jacobian saliency map
Zicong WANG, Jian ZHANG
- Wuhan Digital Engineering Institute, Wuhan 430205, China
-
Received:2024-07-03Online:2025-07-16Published:2025-07-22 -
Contact:Jian ZHANG
CLC Number:
Cite this article
Zicong WANG, Jian ZHANG. Electromagnetic signal no-targeted smooth adversarial attack method based on Jacobian saliency map[J]. Systems Engineering and Electronics, 2025, 47(7): 2127-2135.
share this article
Table 2
Result of model attack with perturbation size set to 0.5"
| 网络模型 | 攻击类型 | 攻击方法 | ASR/% | ATS/s | 扰动比率/% | 最大扰动距离 | COS | 欧氏距离 |
| ResNet | 全局 | FGSM | 89.1 | 0.01 | 99.05 | 0.5 | 83.0 | 22.51 |
| BIM | 94.6 | 0.17 | 80.22 | 0.5 | 97.6 | 7.51 | ||
| C&W | 70.9 | 0.16 | 99.98 | 0.5 | 97.0 | 10.82 | ||
| 局部 | JSMA | 68.1 | 2551.36 | 11.35 | 0.5 | 99.3 | 3.57 | |
| NTSA | 94.8 | 39.13 | 3.47 | 0.5 | 99.4 | 3.54 | ||
| CNN1 | 全局 | FGSM | 90.7 | 0.006 | 100 | 0.5 | 82.9 | 22.63 |
| BIM | 92.2 | 0.05 | 82.99 | 0.5 | 96.3 | 9.36 | ||
| C&W | 79.9 | 0.11 | 99.99 | 0.5 | 96.9 | 10.83 | ||
| 局部 | JSMA | 50.5 | 1764.37 | 12.94 | 0.5 | 99.4 | 4.03 | |
| NTSA | 92.1 | 26.93 | 2.94 | 0.5 | 99.4 | 3.07 | ||
| CNN2 | 全局 | FGSM | 89.9 | 0.007 | 97.06 | 0.5 | 83.1 | 22.22 |
| BIM | 89.5 | 0.08 | 75.59 | 0.5 | 97.1 | 8.18 | ||
| C&W | 80.9 | 0.09 | 99.95 | 0.5 | 96.9 | 10.89 | ||
| 局部 | JSMA | 72.8 | 2194.69 | 11.49 | 0.5 | 99.7 | 3.12 | |
| NTSA | 91.8 | 27.56 | 2.75 | 0.5 | 99.6 | 2.77 |
Table 3
Result of model attack with perturbation size set to 1.0"
| 网络模型 | 攻击类型 | 攻击方法 | ASR/% | ATS/s | 扰动比率/% | 最大扰动距离 | COS | 欧氏距离 |
| ResNet | 全局 | FGSM | 90.7 | 0.006 | 98.93 | 1.0 | 60.2 | 44.99 |
| BIM | 95.5 | 0.14 | 81.90 | 1.0 | 91.8 | 14.67 | ||
| C&W | 85.7 | 0.14 | 99.99 | 1.0 | 87.3 | 29.04 | ||
| 局部 | JSMA | 71.1 | 942.33 | 5.71 | 1.0 | 98.8 | 4.81 | |
| NTSA | 96.8 | 20.56 | 1.59 | 1.0 | 99.1 | 4.44 | ||
| CNN1 | 全局 | FGSM | 90.9 | 0.006 | 99.86 | 1.0 | 59.8 | 45.25 |
| BIM | 92.3 | 0.05 | 81.59 | 1.0 | 88.8 | 17.09 | ||
| C&W | 84.7 | 0.06 | 99.99 | 1.0 | 87.2 | 29.07 | ||
| 局部 | JSMA | 60.2 | 843.86 | 6.03 | 1.0 | 99.5 | 4.51 | |
| NTSA | 94.4 | 8.66 | 0.93 | 1.0 | 99.4 | 3.34 | ||
| CNN2 | 全局 | FGSM | 90.8 | 0.006 | 96.78 | 1.0 | 60.5 | 44.31 |
| BIM | 90.7 | 0.08 | 81.01 | 1.0 | 89.8 | 16.28 | ||
| C&W | 85.4 | 0.09 | 99.93 | 1.0 | 87.1 | 29.26 | ||
| 局部 | JSMA | 75.6 | 695.13 | 4.87 | 1.0 | 99.3 | 4.39 | |
| NTSA | 94.6 | 14.13 | 1.40 | 1.0 | 99.4 | 3.59 |
| 1 | 王雪松,李健兵,徐丰,等.电磁空间信息资源的认知与利用[J].中国科学基金,2021,35(5):682-687. |
| WANGX S,LIJ B,XUF,et al.Cognition and utilization of electromagnetic space information resources[J].China Science Foundation,2021,35(5):682-687. | |
| 2 | LIU Z, MAO H, WU C Y, et al. A convnet for the 2020s[C]//Proc. of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, 2022: 11976-11986. |
| 3 | DOSOVITSKIY A. An image is worth 16x16 words: transformers for image recognition at scale[EB/OL]. [2024-06-03]. http://arXiv:2010.11929, 2020. |
| 4 | HOWARD A G. Mobilenets: efficient convolutional neural networks for mobile vision applications[EB/OL]. [2024-06-03]. http://arXiv:1704.04861, 2017. |
| 5 | HE K M, ZHANG X Y, REN S Q, et al. Deep residual learning for image recognition[C]//Proc. of the IEEE Conference on Computer Vision and Pattern Recognition, 2016: 770-778. |
| 6 | KRIZHEVSKYA,SUTSKEVERI,HINTONG E.ImageNet classification with deep convolutional neural networks[J].Communications of the ACM,2017,60(6):84-90. |
| 7 | O'SHEA T J, CORGAN J, CLANCY T C. Convolutional radio modulation recognition networks[C]//Proc. of the on Engineering Applications of Neural Networks, 2016: 213-226. |
| 8 | O'SHEAT J,ROYT,CLANCYT C.Over-the-air deep learning based radio signal classification[J].IEEE Journal of Selected Topics in Signal Processing,2018,12(1):168-179. |
| 9 | 刘伟,李钦,牛朝阳,等.低信噪比下基于分裂EfficientNet网络的雷达信号调制方式识别[J].电子学报,2023,51(3):675-686. |
| LIUW,LIQ,NIUC Y,et al.Radar signal modulation method recognition based on split EfficientNet network under low signal-to-noise ratio[J].Chinese Journal of Electronics,2023,51(3):675-686. | |
| 10 | GOODFELLOW I J, SHLENS J, SZEGEDY C. Explaining and harnessing adversarial examples[EB/OL]. [2024-06-03]. http://arXiv:1412.6572, 2014. |
| 11 | QIANY G,ZHANGX M,WANGB,et al.Adversarial training defense based on second-order adversarial examples[J].Journal of Electronics & Information Technology,2021,43(11):3367-3373. |
| 12 | 赵宏佳, 张多纳, 鲁远耀, 等. 领域知识内嵌的电磁信号调制方式智能识别[EB/OL]. [2024-06-03]. https://doi.org/10.13700/j.bh.1001-5965.2023.0746. |
| ZHAO H J, ZHANG D N, LU Y Y, et al. Intelligent recognition of electromagnetic signal modulation mode embedded in domain knowledge[EB/OL]. [2024-06-03]. https://doi.org/10.13700/j.bh.1001-5965.2023.0746. | |
| 13 | SZEGEDY C, ZAREMBA W, SUTSKEVER I, et al. Intriguing properties of neural networks[C]//Proc. of the 2nd Inter-national Conference on Learning Representations, 2014. |
| 14 | YE N, LI Q, ZHOU X Y, et al. Amata: an annealing mechanism for adversarial training acceleration[C]//Proc. of the AAAI Conference on Artificial Intelligence, 2021. |
| 15 | LINY,ZHAOH J,MAX F,et al.Adversarial attacks in modulation recognition with convolutional neural networks[J].IEEE Trans.on Reliability,2020,70(1):389-401. |
| 16 | ZHAO H J, LIN Y, GAO S, et al. Evaluating and improving adversarial attacks on DNN-based modulation recognition[C]// Proc. of the Globecom IEEE Global Communications Conference, 2021. |
| 17 | KURAKIN A, GOODFELLOW I J, BENGIO S. Adversarial examples in the physical world[EB/OL]. [2024-06-03]. https://arxiv.org/abs/1607.02533?context=cs. |
| 18 | MOOSAVI-DEZFOOLI S M, FAWZI A, FROSSARD P. Deepfool: a simple and accurate method to fool deep neural networks[C]//Proc. of the IEEE Conference On Computer Vision and Pattern Recognition, 2016: 2574-2582. |
| 19 | MA R, ZHU C, LU M, et al. Concealed electronic countermeasures of radar signal with adversarial examples[EB/OL]. [2024-06-03]. http://arXiv:2310.08292, 2023. |
| 20 | PAPERNOT N, MCDANIEL P, JHA S, et al. The limitations of deep learning in adversarial settings[C]//Proc. of IEEE European Symposium on Security and Privacy, 2016: 372-387. |
| 21 | 周侠,张剑,李宁安.基于显著图的电磁信号对抗样本生成方法[J].电子学报,2023,51(7):1917-1928. |
| ZHOUX,ZHANGJ,LIN A.Electromagnetic signal adversarial example generation method based on saliency graph[J].Chinese Journal of Electronics,2023,51(7):1917-1928. | |
| 22 | 李哲铭,王晋东,侯建中,等.基于显著区域优化的对抗样本攻击方法[J].计算机工程,2023,49(9):246-255, 264. |
| LIZ M,WANGJ D,HOUJ Z,et al.Adversarial sample attack method based on significant region optimization[J].Computer Engineering,2023,49(9):246-255, 264. | |
| 23 | 王满喜,史明佳,陆科宇,等.电磁信号调制识别中的对抗性攻击技术研究[J].无线电通信技术,2022,48(6):1098-1104. |
| WANGM X,SHIM J,LUK Y,et al.Research on adversarial attack technology in electromagnetic signal modulation and recognition[J].Radio Communication Technology,2022,48(6):1098-1104. | |
| 24 | 张多纳,赵宏佳,鲁远耀,等.电磁信号调制方式识别: 现状、方法和展望[J].信息与控制,2023,52(1):59-74. |
| ZHANGD N,ZHAOH J,LUY Y,et al.Radio signal modulation recognition: research, methods and prospects[J].Information and Control,2023,52(1):59-74. | |
| 25 | 黄知涛,柯达,王翔.电磁信号对抗样本攻击与防御发展研究[J].信息对抗技术,2023,2(4):37-52. |
| HUANGZ T,KED,WANGX.Research on the development of electromagnetic signal countermeasure sample attack and defense[J].Information Countermeasure Technology,2023,2(4):37-52. | |
| 26 | 韩超,秦若熙,王林元,等.无线通信中的智能识别神经网络对抗攻击技术综述[J].电讯技术,2023,63(6):918-926. |
| HANC,QINR X,WANGL Y,et al.A review of intelligent recognition neural network adversarial attack technology in wireless communication[J].Tele-Communication Technology,2023,63(6):918-926. | |
| 27 | ZHANGF X,LUOC C,XUJ L,et al.Deep learning based automatic modulation recognition: models, datasets, and challenges[J].Digital Signal Processing,2022,129,103650. |
| 28 | KE D, HUANG Z T, WANG X, et al. Application of adver sarial examples in communication modula-tion classification[C]// Proc. of the International Conference on Data Mining Workshops, 2019: 877-882. |
| 29 | CARLINI N, WAGNER D. Towards evaluating the robustness of neural networks[C]//Proc. of the IEEE Symposium on Security and Privacy, 2017: 39-57. |
| [1] | Jianguo YIN, Wen SHENG, Wei JIANG. Radar air target recognition based on deep residual shrinkage network [J]. Systems Engineering and Electronics, 2024, 46(9): 3012-3018. |
| [2] | Jiyuan CHEN, Zhenhai XU, Shunping XIAO. Robust interference suppression of wideband irregular subarrayed phased array based on subarray level processing [J]. Systems Engineering and Electronics, 2024, 46(2): 367-380. |
| [3] | Yun ZHONG, Lujun WAN, Peiyang YAO, Jieyong ZHANG. Measurement and optimization of generation and evolution of agile C2 organization [J]. Systems Engineering and Electronics, 2023, 45(4): 1090-1097. |
| [4] | Tianqi ZHANG, Shaopeng YE, Jianxing LIU, Haojun BAI. Frequency centroid zero watermarking algorithm based on Tetrolet transform of color image [J]. Systems Engineering and Electronics, 2023, 45(1): 41-48. |
| [5] | Haoyang LI, Jianjun XIANG, Fang PENG, Shuai WANG, Zhijun LI. Beam space generalized sidelobe canceller algorithm based on particle swarm optimization [J]. Systems Engineering and Electronics, 2022, 44(10): 3037-3045. |
| [6] | Zhirou YANG, Hu ZHANG, Jing LIU, Tonglin LIU. Optimization algorithm of military communication network structure under node attack strategy [J]. Systems Engineering and Electronics, 2021, 43(7): 1848-1855. |
| [7] | Zhe WANG, Jianhua LI, Dong KANG. Robustness of two-layer heterogeneous interdependent network model for networked information system of system [J]. Systems Engineering and Electronics, 2021, 43(4): 961-969. |
| [8] | Chao WANG, Jilian GUO, Anwei SHEN. Analysis of cascading failures of interdependent networks based on asymmetric dependency [J]. Systems Engineering and Electronics, 2020, 42(5): 1093-1101. |
| [9] | Qiao CHEN, Ningning TONG, Xiaowei HU, Shanshan DING. Non-ideal orthogonal waveforms imaging of MIMO radar based on multiple measurement vector block sparse algorithm [J]. Systems Engineering and Electronics, 2020, 42(12): 2747-2754. |
| [10] | CHEN Wu, FAN Mingkai, LI Zehong, JIN Xin, HONG Liang. Design of network robustness for drone swarm system [J]. Systems Engineering and Electronics, 2019, 41(11): 2633-2640. |
| [11] | WANG Ershen, WANG Yuwei, QU Pingping, LAN Xiaoyu, CHEN Jiamei. Effectiveness analysis of complex network edge attack strategy with cost [J]. Systems Engineering and Electronics, 2018, 40(4): 919-926. |
| [12] | XU Qiuping, WANG Xugang, WANG Zhongyuan. Design of attitude decoupling controller for gliding guided projectile based on active disturbance rejection control [J]. Systems Engineering and Electronics, 2018, 40(2): 384-392. |
| [13] | SI Guangya, WANG Fei, LI Cong, ZHANG Yu. Robustness assessment method for armament system of systems based on measuring of interaction network [J]. Systems Engineering and Electronics, 2017, 39(7): 1506-1512. |
| [14] | WANG Junde, LAO Songyang, RUAN Yirun, HOU Lülin, BAI Liang. Research on robustness of interdependent networks based on load tolerance of nodes [J]. Systems Engineering and Electronics, 2017, 39(11): 2477-2483. |
| [15] | SUN Shiyan, ZHU Huimin. PROMETHEE’s parameters setting method based on robustness analysis [J]. Systems Engineering and Electronics, 2017, 39(1): 120-124. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||