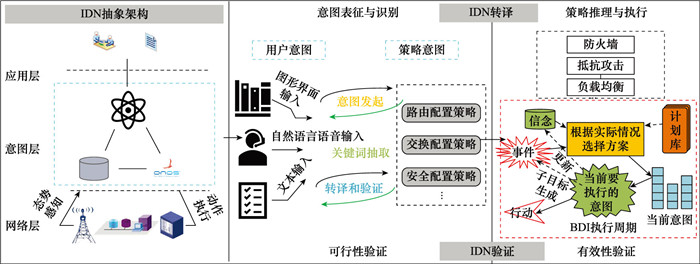
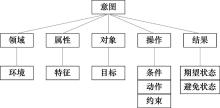
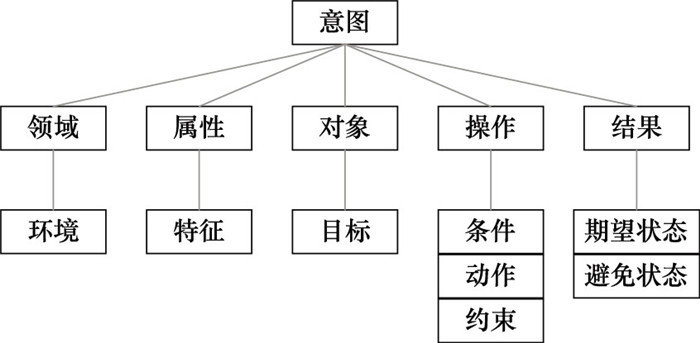
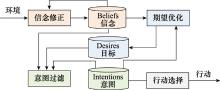
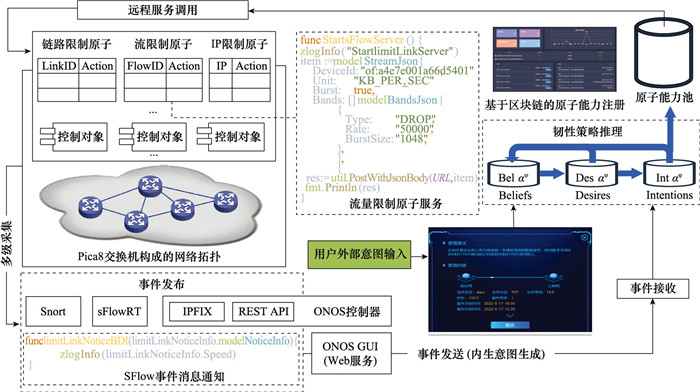
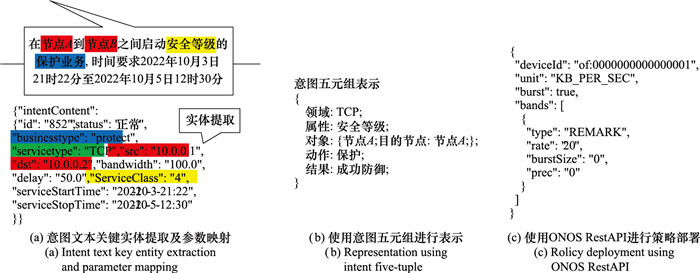
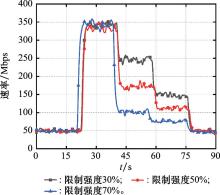
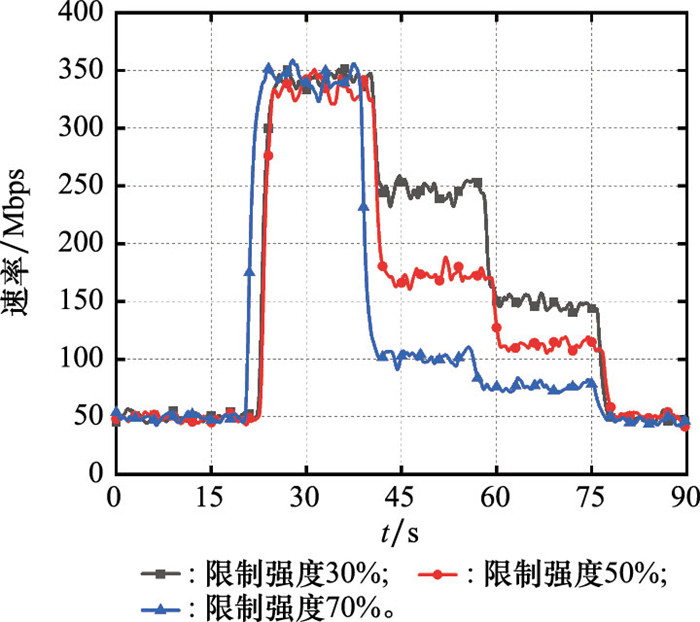
Systems Engineering and Electronics ›› 2024, Vol. 46 ›› Issue (9): 3211-3220.doi: 10.12305/j.issn.1001-506X.2024.09.32
• Communications and Networks • Previous Articles
Research on intent-driven resilience network security
Yanbo SONG1, Xianming GAO2, Chungang YANG1,3,*, Pengcheng LI3
- 1. School of Telecommunications Engineering, Xidian University, Xi'an 710071, China
2. Institute of System Engineering Academy of Military Sciences, Beijing 100039, China
3. Hangzhou Institute of Technology, Xidian University, Hangzhou 311200, China
-
Received:2023-07-28Online:2024-08-30Published:2024-09-12 -
Contact:Chungang YANG
CLC Number:
Cite this article
Yanbo SONG, Xianming GAO, Chungang YANG, Pengcheng LI. Research on intent-driven resilience network security[J]. Systems Engineering and Electronics, 2024, 46(9): 3211-3220.
share this article
| 1 |
YOU X H , WANG C X , HUANG J , et al. Towards 6G wireless communication networks: vision, enabling technologies, and new paradigm shifts[J]. Science China Information Sciences, 2021, 64, 110301.
doi: 10.1007/s11432-020-2955-6 |
| 2 |
PANG L , YANG C G , CHEN D Y , et al. A survey on intent-driven networks[J]. IEEE Access, 2020, 8, 22862- 22873.
doi: 10.1109/ACCESS.2020.2969208 |
| 3 |
SONG Y B , YANG C G , ZHANG J M , et al. Full-life cycle intent-driven network verification: challenges and approaches[J]. IEEE Network, 2023, 37 (5): 145- 153.
doi: 10.1109/MNET.124.2200127 |
| 4 |
MEHMOOD K , KRALEVSKA K , PALMA D . Intent-driven autonomous network and service management in future networks: a structured literature review[J]. Computer Networks, 2023, 220, 109477.
doi: 10.1016/j.comnet.2022.109477 |
| 5 |
KIM J , KIM E , YANG J , et al. IBCS: intent-based cloud services for security applications[J]. IEEE Communications Magazine, 2020, 58 (4): 45- 51.
doi: 10.1109/MCOM.001.1900476 |
| 6 | TIAN B C, ZHANG X Y, ZHAI E N, et al. Safely and automatically updating in-network ACL configurations with intent language[C]//Proc. of the ACM Special Interest Group on Data Communication, 2019: 214-226. |
| 7 | CHUNG C, JEONG J P. A design of IoT device configuration translator for intent-based IoT-cloud services[C]//Proc. of the 22nd International Conference on Advanced Communication Techno-logy, 2020: 52-56. |
| 8 | OpenDayLight. Nemo user guide[EB/OL]. [2023-05-11]. http://test-odl-docs.readthedocs.io/en/latest/user-guide/nemo-user-guide.html. |
| 9 |
CHOWDHARY A , SABUR A , VADNERE N , et al. Intent-driven security policy management for software-defined systems[J]. IEEE Trans.on Network and Service Management, 2022, 19 (4): 5208- 5223.
doi: 10.1109/TNSM.2022.3183591 |
| 10 | SCHEID J, MACHADO C, FRANCO F, et al. INSpIRE: integrated NFV-based intent refinement environment[C]//Proc. of the IFIP/IEEE Symposium on Integrated Network and Service Management, 2017: 186-194. |
| 11 | ABHASHKUMAR A, KANG J M, BANERJEE S, et al. Supporting diverse dynamic intent-based policies using JANUS[C]// Proc. of the 13th International Conference on Emerging Networking Experiments and Technologies, 2017, 14: 296-309. |
| 12 |
YANG C G , MI X R , OUYANG Y , et al. SMART intent-driven network management[J]. IEEE Communications Magazine, 2023, 61 (1): 106- 112.
doi: 10.1109/MCOM.002.2200119 |
| 13 |
LIYANAGE M , PHAM Q V , DEV K , et al. A survey on zero touch network and service management (ZSM) for 5G and beyond networks[J]. Journal of Network and Computer Applications, 2022, 203, 103362.
doi: 10.1016/j.jnca.2022.103362 |
| 14 |
MEHMOOD K , KRALEVSKA K , PALMA D . Intent-driven autonomous network and service management in future cellular networks: a structured literature review[J]. Computer Networks, 2023, 220, 109477.
doi: 10.1016/j.comnet.2022.109477 |
| 15 |
LIU X M , LI D Q , MA M Q , et al. Network resilience[J]. Physics Reports, 2022, 971, 1- 108.
doi: 10.1016/j.physrep.2022.04.002 |
| 16 | ZEYDAN E, TURK Y. Recent advances in intent-based networking: a survey[C]//Proc. of the IEEE 91st Vehicular Technology Conference, 2020. |
| 17 | AREZOUMAND S, DZEPAROSKA K, BANNAZADEH H, et al. MD-IDN: Multi-domain intent-driven networking in software-defined infrastructures[C]//Proc. of the 13th International Conference on Network and Service Management, 2017. |
| 18 | SHAGHAGHI A, KAAFAR M A, BUYYA R. Software-defined network (SDN) data plane security: issues, solutions, and future directions[M]. GUPTA B, PEREZ G, AGRAWAI D, et al, ed. Cham: Handbook of Computer Networks and Cyber Security, 2020: 341-387. |
| 19 | 张佳鸣, 杨春刚, 庞磊, 等. 意图物联网[J]. 物联网学报, 2019, 3 (3): 5- 10. |
| ZHANG J M , YANG C G , PANG L , et al. Intent driven Internet of Things[J]. Chinese Journal on Internet of Things, 2019, 3 (3): 5- 10. | |
| 20 | 何发智, 吕晓, 蔡维纬. 支持操作意图一致性的实时协同编辑算法综述[J]. 计算机学报, 2018, 41 (4): 840- 867. |
| HE F Z , LYU X , CAI W W . Survey of real-time collaborative editing algorithms supporting operation intention consistency[J]. Chinese Journal of Computer, 2018, 41 (4): 840- 867. | |
| 21 | ADDAD R, DUTRA D, BAGAA M. Benchmarking the ONOS Intent interfaces to ease 5G service management[C]//Proc. of the IEEE Global Communications Conference, 2018. |
| 22 | RFC 8994. An autonomic control plane (ACP)[S]. New York: Internet Engineering Task Force, 2021. |
| 23 | JACOBS S, PFITSCHER J, RIBEIRO H. Deploying natural language intents with lumi[C]//Proc. of the ACM SIGCOMM Conference Posters and Demos, 2019: 82-84. |
| 24 | JACOBS A, FERREIRA R, PITSCHER R. Refining network intents for self-driving networks[C]//Proc. of the Afternoon Workshop on Self-Driving Networks, 2018: 15-21. |
| 25 | 朱梦迪, 束永安. 软件定义网络中控制数据平面一致性的验证[J]. 计算机应用, 2020, 40 (6): 1751- 1754. |
| ZHU M D , SHU Y A . Verification of control-data plane consistency in software defined network[J]. Journal of Computer Applications, 2020, 40 (6): 1751- 1754. | |
| 26 | 王敬宇, 周铖, 张蕾, 等. 知识定义的意图网络自治[J]. 电信科学, 2021, 37 (9): 1- 13. |
| WANG J Y , ZHOU C , ZHANG L , et al. Knowledge-defined intent-based network autonomy[J]. Telecommunications Science, 2021, 37 (9): 1- 13. | |
| 27 |
NUNES I , SCHARDONG F , SCHAEFFER-FILHO A . BDI2DoS: an application using collaborating BDI agents to combat DDoS attacks[J]. Journal of Network and Computer Applications, 2017, 84, 14- 24.
doi: 10.1016/j.jnca.2017.01.035 |
| 28 |
CHOWDHARY A , SABUR A , VADNERE N , et al. Intent-dri-ven security policy management for software-defined systems[J]. IEEE Trans.on Network Service Management, 2022, 19 (4): 5208- 5223.
doi: 10.1109/TNSM.2022.3183591 |
| 29 | OOI E , BEURAN R , KURODA T , et al. Intent-driven secure system design: methodology and implementation[J]. Computers & Security, 2023, 124, 102955. |
| 30 | SHARMA Y , BHAMARE D , SASTRY N , et al. SLA management in intent-driven service management systems: a taxonomy and future directions[J]. ACM Computing Surveys, 2023, 55 (13): 292. |
| 31 | LARA A , KOLASANI A , RAMAMURTHY B . Network innovation using openflow: a survey[J]. IEEE Communications Surveys & Tutorials, 2013, 16 (1): 493- 512. |
| [1] | Xianglin LIU, Chungang YANG, Fuqiang LI, Ying OUYANG, Yanbo SONG. Intent-driven data link network policy negotiation model and algorithm [J]. Systems Engineering and Electronics, 2024, 46(6): 2128-2137. |
| [2] | Zeyang JI, Chungang YANG, Fuqiang LI, Ying OUYANG, Xianglin LIU. Intent-driven network representation based on natural language processing [J]. Systems Engineering and Electronics, 2024, 46(1): 318-325. |
| [3] | Xinxin RU, Xiaoguang GAO, Yangyang WANG. Bayesian network parameter learning based on fuzzy constraints [J]. Systems Engineering and Electronics, 2023, 45(2): 444-452. |
| [4] | Junfeng SUN, Chenghai LI, Bo CAO. Network security situation prediction based on TCN-BiLSTM [J]. Systems Engineering and Electronics, 2023, 45(11): 3671-3679. |
| [5] | Jiacai YI, Bin LIU, Li YAO, Wentao ZHAO. Satellite cyber situational understanding based on knowledge reasoning [J]. Systems Engineering and Electronics, 2022, 44(5): 1562-1571. |
| [6] | Zhigang JIN, Tong WU. Intrusion detection based on feature selection and tree Parzen estimation [J]. Systems Engineering and Electronics, 2021, 43(7): 1954-1960. |
| [7] | Chunrong HE, Jiang ZHU. Security situation prediction method of GRU neural network [J]. Systems Engineering and Electronics, 2021, 43(1): 258-266. |
| [8] | LI Fangwei, LI Junyao, NIE Yifang, ZHU Jiang. Dynamic trust situation awareness mechanism based on multiagent system [J]. Systems Engineering and Electronics, 2017, 39(5): 1148-1153. |
| [9] | QIAN Yu-wen, SONG Hua-ju, ZHAO Bang-xin, ZHANG Tong-fang,HAO Jin-song. Study on the detection algorithm of covert network behavior channel based on corrected entropy [J]. Journal of Systems Engineering and Electronics, 2013, 35(6): 1312-1217. |
| [10] | WANG Bin1,2,3, WU Qinzhang1, WANG Chunhong1, SUN Yongquan3, DU Zhongpi. High trusted computer based on security control module [J]. Journal of Systems Engineering and Electronics, 2010, 32(2): 437-440. |
| [11] | WANG Jie, SHI Cheng-hui, LIU Ya-bin. Efficient dynamic packet filtering program based on shared-node counting Bloom filter [J]. Journal of Systems Engineering and Electronics, 2009, 31(9): 2227-2231. |
| [12] | DU Zhi-qiang, SHEN Yu-long, MA Jian-feng, ZHOU Li-hua. AKB-OTS based broadcast authentication protocol for sensor networks [J]. Journal of Systems Engineering and Electronics, 2009, 31(8): 2008-2012. |
| [13] | QIN Hua-wang, DAI Yue-wei, WANG Zhi-quan. Model of distributed intrusion tolerant system based on Petri net [J]. Journal of Systems Engineering and Electronics, 2009, 31(1): 208-212. |
| [14] | QIN Hua-wang, DAI Yue-wei, WANG Zhi-quan. Model of distributed intrusion tolerant system based on Petri net [J]. Journal of Systems Engineering and Electronics, 2009, 31(01): 208-212. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||