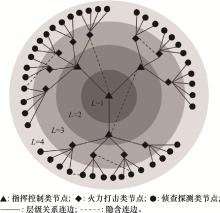
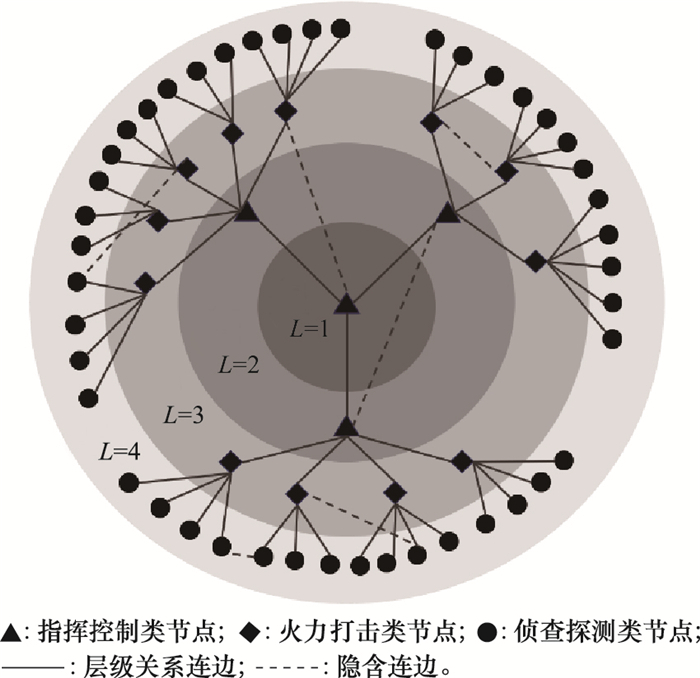
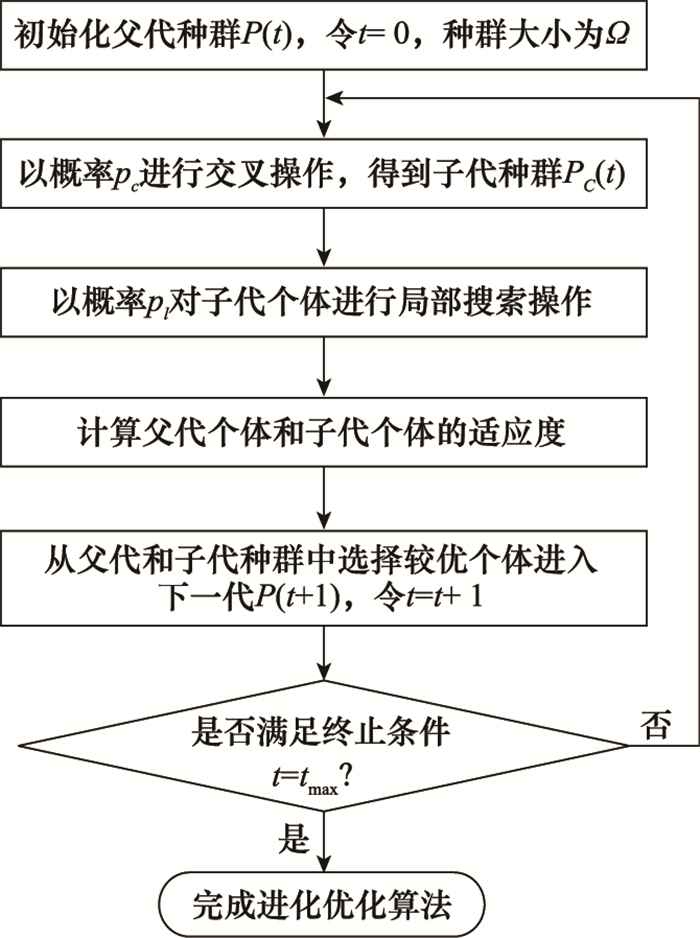
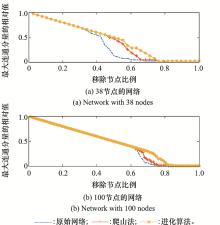
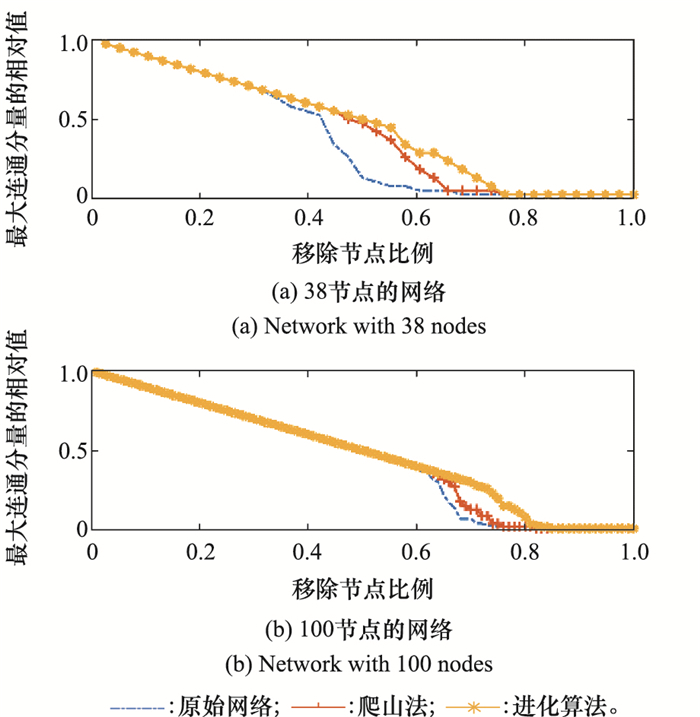
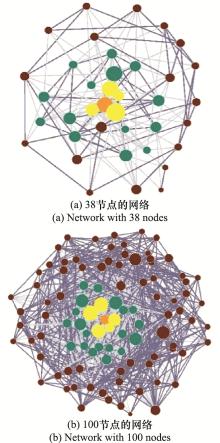
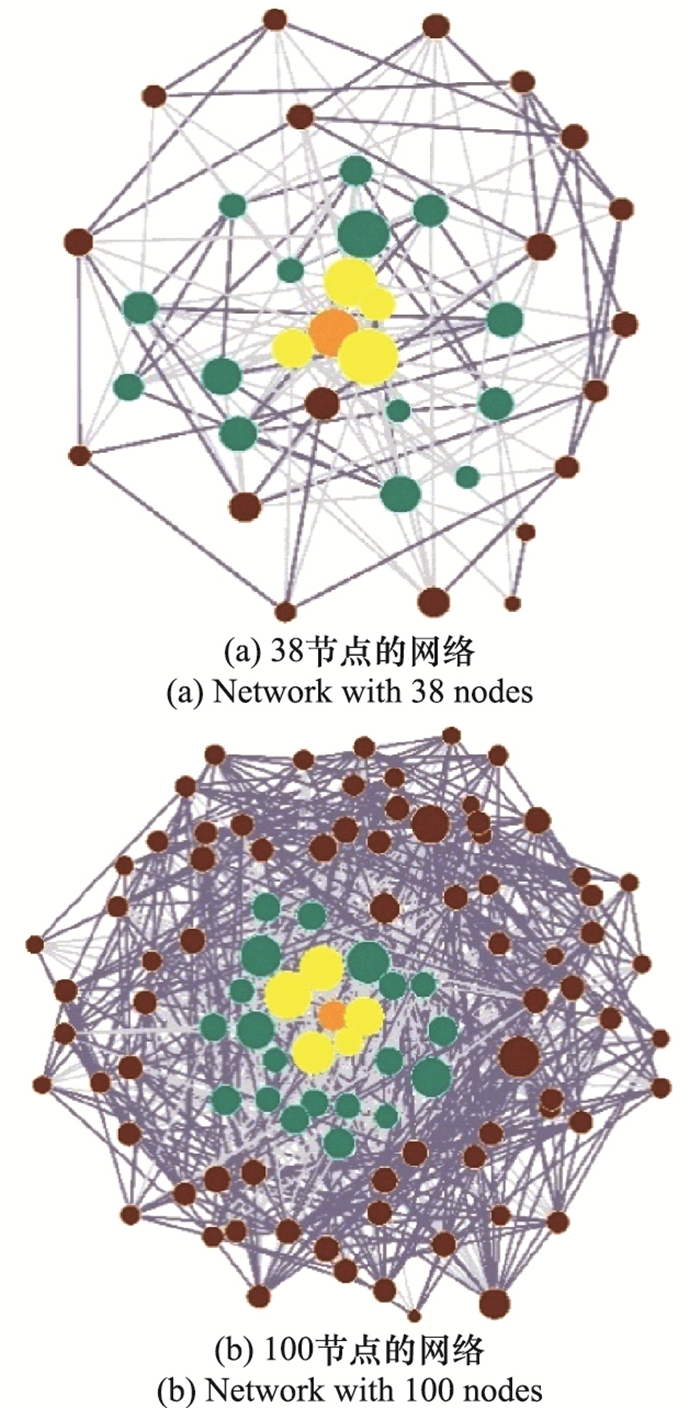
Systems Engineering and Electronics ›› 2021, Vol. 43 ›› Issue (7): 1848-1855.doi: 10.12305/j.issn.1001-506X.2021.07.16
• Systems Engineering • Previous Articles Next Articles
Optimization algorithm of military communication network structure under node attack strategy
Zhirou YANG1, Hu ZHANG2,*, Jing LIU1, Tonglin LIU2
- 1. School of Artificial Intelligence, Xidian University, Xi'an 710071, China
2. Beijing Electro-mechanical Engineering Institute, Beijing 100074, China
-
Received:2020-08-18Online:2021-06-30Published:2021-07-08 -
Contact:Hu ZHANG
CLC Number:
Cite this article
Zhirou YANG, Hu ZHANG, Jing LIU, Tonglin LIU. Optimization algorithm of military communication network structure under node attack strategy[J]. Systems Engineering and Electronics, 2021, 43(7): 1848-1855.
share this article
| 1 |
CHEN G Y , SUN P , ZHANG J Y . Repair strategy of military communication network based on discrete artificial bee colony algorithm[J]. IEEE Access, 2020, 8, 73051- 73060.
doi: 10.1109/ACCESS.2020.2987860 |
| 2 | HE Z Q, WANG L H, LIU W F. Model and effectiveness analysis for C4ISR system structure based on complex network[C]//Proc. of the 10th in International Conference on Intelligent Human Machine Systems and Cybernetics, 2018. |
| 3 |
CHAN K S , JOHNSEN F T . Military communications and networks[J]. IEEE Communications Magazine, 2020,
doi: 10.1109/MCOM.2020.9183742 |
| 4 | XIN B , WANG Y P , CHEN J . An efficient marginal-return-based constructive heuristic to solve the sensor-weapon-target assignment problem[J]. IEEE Trans.on Systems, Man, and Cybernetics: Systems, 2018, 49 (12): 2536- 2547. |
| 5 | LIU J X . A regulative arithmetic on the contingency communication in the damaged military communication network[J]. Applied Mechanics and Materials, 2014, 364, 571- 572. |
| 6 |
PARK C , PATTIPATI K R , AN W , et al. Quantifying the impact of information and organizational structures via distributed auction algorithm: point-to-point communication structure[J]. IEEE Trans.on System Man and Cybernetics Part A Systems and Humans, 2012, 42 (1): 68- 86.
doi: 10.1109/TSMCA.2011.2157139 |
| 7 |
GAO X E , LI K Q , CHEN B . Invulnerability measure of a military heterogeneous network based on network structure entropy[J]. IEEE Access, 2018, 6, 6700- 6708.
doi: 10.1109/ACCESS.2017.2769964 |
| 8 |
TORLEIV M , RANDALL L . Network centric military communications[J]. IEEE Communication Magazine, 2008, 46 (11): 30- 32.
doi: 10.1109/MCOM.2008.4689241 |
| 9 | SONG X , SHI W , TAN G , et al. Multi-level tolerance opinion dynamics in military command and control networks[J]. Physica A: Statal Mechanics and its Applications, 2015, 473, 322- 332. |
| 10 |
ANAND K , BIANCONI G . Entropy measures for networks: toward an information theory of complex topologies[J]. Physical Review E, 2009, 80 (4): 045102.
doi: 10.1103/PhysRevE.80.045102 |
| 11 | SCHEIDT D, SCHULTZ K. On optimizing command and control structures[C]//Proc. of the 16th International Command and Control Research and Technology Symposium, 2011. |
| 12 |
LU Y , ZHAO Y J , SUN F C , et al. Measuring and improving communication robustness of networks[J]. IEEE Communications Letters, 2019, 23 (12): 2168- 2171.
doi: 10.1109/LCOMM.2019.2941940 |
| 13 | WEN R, CHEN X Q, DONG Z B, et al. Modeling for military system by weighted complex networks[C]//Proc. of the IEEE International Conference on Control and Automation, 2010. |
| 14 | LIU J X, CHEN S D, WANG Y G. Study on node importance of complex network based military command control networks[C]//Proc. of the International Conference on Machine Learning and Cybernetics, 2012. |
| 15 | QI Y B , LIU Z , CHEN H D , et al. Distributed combat system of systems network modeling[J]. Journal of Networks, 2013, 8 (8): 1906- 1912. |
| 16 | 石福丽. 基于超网络的军事通信网络建模、分析与重构方法研究[D]. 长沙: 国防科学技术大学, 2013. |
| SHI F L. Research on super network based modeling and analysis for military communication network reconfiguration[D]. Changsha: National University of Defense Technology, 2013. | |
| 17 |
LI J C , JIANG J , YANG K W , et al. Research on functional robustness of heterogeneous combat networks[J]. IEEE Systems Journal, 2019, 13 (2): 1487- 1495.
doi: 10.1109/JSYST.2018.2828779 |
| 18 | DEKKER A H . Measuring the agility of networked military forces[J]. Journal of Battlefield Technology, 2006, 9 (1): 19- 24. |
| 19 | CARES J R. An information age combat model[R]. U.S. : Produced for the United States Office of the Secretary of Defense, 2004. |
| 20 |
朱刚, 谭贤四, 王红, 等. NSHT预警装备体系网络化建模与分析[J]. 火力与指挥控制, 2015, 40 (2): 118- 122.
doi: 10.3969/j.issn.1002-0640.2015.02.029 |
|
ZHU G , TAN X S , WANG H , et al. NSHT early warning system-of-systems networked modeling and analyzing[J]. Fire Control and Command Control, 2015, 40 (2): 118- 122.
doi: 10.3969/j.issn.1002-0640.2015.02.029 |
|
| 21 |
李尔玉, 龚建兴, 黄健, 等. 基于功能链的作战体系复杂网络节点重要性评价方法[J]. 指挥与控制学报, 2018, 4 (1): 42- 49.
doi: 10.3969/j.issn.2096-0204.2018.01.0042 |
|
LI E Y , GONG J X , HUANG J , et al. Node importance analysis of complex networks for combat systems based on function chain[J]. Journal of Command and Control, 2018, 4 (1): 42- 49.
doi: 10.3969/j.issn.2096-0204.2018.01.0042 |
|
| 22 | 邢焕革, 彭义波. 条件攻击策略下作战体系网络抗打击性能分析[J]. 计算机工程与设计, 2015, 36 (4): 866- 871. |
| XING H G , PENG Y B . Anti-attack performance analysis of combat system network under selectivity attack strategy[J]. Computer Engineering and Design, 2015, 36 (4): 866- 871. | |
| 23 | JIN W X, SONG P, LIU G Z. The vulnerability of the military SOS networks under different attack and defense strategies[C]//Proc. of the IEEE International Conference on Service Operations and Logistics and Informatics, 2014: 68-75. |
| 24 | SCHNEIDER C M , ANDRE A M , JOSE S , et al. Onion-like network topology enhance robustness against malicious attacks[J]. Journal of Statistical Mechanics: Theory and Experiment, 2011, 1, P01027. |
| 25 |
QIU T , ZHAO A Y , XIA F , et al. Rose: robustness strategy for scale-free wireless sensor networks[J]. IEEE/ACM Trans.on Networking, 2017, 25 (5): 2944- 2959.
doi: 10.1109/TNET.2017.2713530 |
| 26 |
QIU T , LIU J , SI W S , et al. Robustness optimization scheme with multi-population co-evolution for scale-free wireless sensor networks[J]. IEEE/ACM Trans.on Networking, 2019, 27 (3): 1028- 1042.
doi: 10.1109/TNET.2019.2907243 |
| 27 |
WANG S , LIU J , JIN Y C . A computationally efficient evolutionary algorithm for multi-objective network robustness optimization[J]. IEEE Trans.on Evolutionary Computation, 2021,
doi: 10.1109/TEVC.2020.3048174 |
| 28 |
WANG S , LIU J , JIN Y C . Surrogate-assisted robust optimization of large-scale networks based on graph embedding[J]. on Evolutionary Computation, 2020, 24 (4): 735- 749.
doi: 10.1109/TEVC.2019.2950935 |
| 29 |
ZHOU M X , LIU J . A memetic algorithm for enhancing the robustness of scale-free networks against malicious attacks[J]. Physica A: Statistical Mechanics and its Applications, 2014, 410, 131- 143.
doi: 10.1016/j.physa.2014.05.002 |
| 30 | 汪小帆, 李翔, 陈关荣. 复杂网络理论及其应用[M]. 北京: 清华大学出版社, 2006. |
| WANG X F , LI X , CHEN G R . Complex network and its application[M]. Beijing: Tsinghua Press, 2006. |
| [1] | Haoyang LI, Jianjun XIANG, Fang PENG, Shuai WANG, Zhijun LI. Beam space generalized sidelobe canceller algorithm based on particle swarm optimization [J]. Systems Engineering and Electronics, 2022, 44(10): 3037-3045. |
| [2] | Zhe WANG, Jianhua LI, Dong KANG. Robustness of two-layer heterogeneous interdependent network model for networked information system of system [J]. Systems Engineering and Electronics, 2021, 43(4): 961-969. |
| [3] | Chao WANG, Jilian GUO, Anwei SHEN. Analysis of cascading failures of interdependent networks based on asymmetric dependency [J]. Systems Engineering and Electronics, 2020, 42(5): 1093-1101. |
| [4] | Qiao CHEN, Ningning TONG, Xiaowei HU, Shanshan DING. Non-ideal orthogonal waveforms imaging of MIMO radar based on multiple measurement vector block sparse algorithm [J]. Systems Engineering and Electronics, 2020, 42(12): 2747-2754. |
| [5] | Tonglin LIU, Zhirou YANG, Hu ZHANG, Xiangyi TENG, Jing LIU. Modeling and performance analysis of military communication network [J]. Systems Engineering and Electronics, 2020, 42(12): 2892-2898. |
| [6] | CHEN Wu, FAN Mingkai, LI Zehong, JIN Xin, HONG Liang. Design of network robustness for drone swarm system [J]. Systems Engineering and Electronics, 2019, 41(11): 2633-2640. |
| [7] | WANG Ershen, WANG Yuwei, QU Pingping, LAN Xiaoyu, CHEN Jiamei. Effectiveness analysis of complex network edge attack strategy with cost [J]. Systems Engineering and Electronics, 2018, 40(4): 919-926. |
| [8] | XU Qiuping, WANG Xugang, WANG Zhongyuan. Design of attitude decoupling controller for gliding guided projectile based on active disturbance rejection control [J]. Systems Engineering and Electronics, 2018, 40(2): 384-392. |
| [9] | SI Guangya, WANG Fei, LI Cong, ZHANG Yu. Robustness assessment method for armament system of systems based on measuring of interaction network [J]. Systems Engineering and Electronics, 2017, 39(7): 1506-1512. |
| [10] | MA Longbang, GUO Ping, ZHAO Juan. Node protection capability based survivability assessment method for command and control system network [J]. Systems Engineering and Electronics, 2017, 39(7): 1524-1531. |
| [11] | WANG Junde, LAO Songyang, RUAN Yirun, HOU Lülin, BAI Liang. Research on robustness of interdependent networks based on load tolerance of nodes [J]. Systems Engineering and Electronics, 2017, 39(11): 2477-2483. |
| [12] | SUN Shiyan, ZHU Huimin. PROMETHEE’s parameters setting method based on robustness analysis [J]. Systems Engineering and Electronics, 2017, 39(1): 120-124. |
| [13] | ZHANG Jie-yong, YI Kan, WANG Heng, ZHANG Jin-feng, ZHOU Xiang-xiang. Dynamic robustness measure method considering cascading failure for C4ISR system structure [J]. Systems Engineering and Electronics, 2016, 38(9): 2072-2079. |
| [14] | LI Min, WANG Song-yan, ZHANG Ying-chun, LI Hua-yi. Satellite autonomous navigation filtering algorithm based on improved strong tracking square-root UKF [J]. Systems Engineering and Electronics, 2015, 37(8): 1858-1865. |
| [15] | SHEN Di, LI Jian-hua, ZHANG Qiang, ZHU Rui. Research on military information grid cascading failure model and robustness strategy [J]. Systems Engineering and Electronics, 2015, 37(2): 310-317. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||