Systems Engineering and Electronics ›› 2024, Vol. 46 ›› Issue (12): 4128-4139.doi: 10.12305/j.issn.1001-506X.2024.12.21
• Systems Engineering • Previous Articles
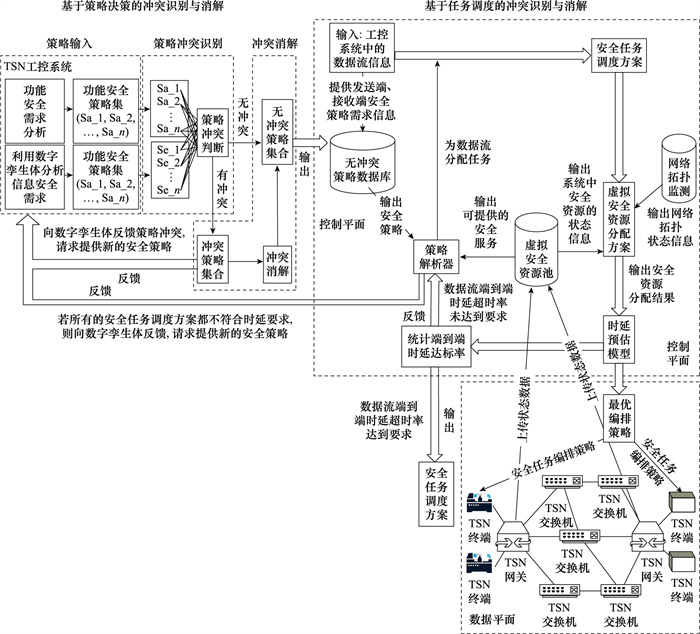
Conflict resolution method for security strategies for TSN industrial control system
Zhitong WANG1, Xiaoya HU1,2,*
- 1. School of Artificial Intelligence and Automation, Huazhong University of Science and Technology, Wuhan 430074, China
2. Shenzhen Research Institute of Huazhong University of Science and Technology, Shenzhen 518057, China
-
Received:2024-02-26Online:2024-11-25Published:2024-12-30 -
Contact:Xiaoya HU
CLC Number:
Cite this article
Zhitong WANG, Xiaoya HU. Conflict resolution method for security strategies for TSN industrial control system[J]. Systems Engineering and Electronics, 2024, 46(12): 4128-4139.
share this article
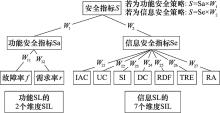
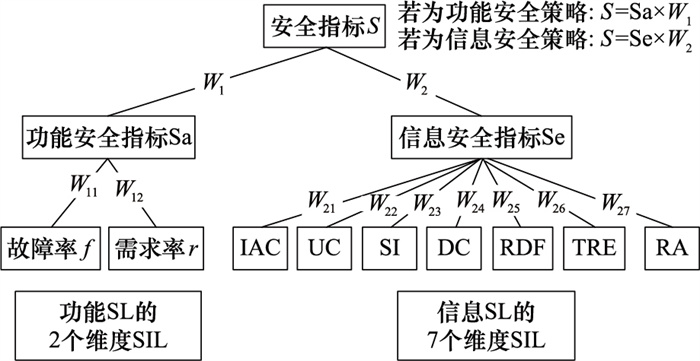
Table 5
Mathematical symbols explanation"
| 符号 | 形式/计算方法 | 说明 |
| listtaski | [tasks1, tasks2, …, tasksn] | 第i种数据流的任务组合集合 |
| Policyi·LeT | - | 安全策略Policyi的SL |
| tasksij·LeC | - | 安全任务tasksij的SL |
| Lei | 每种数据流的安全指标 | |
| Le | minLei | 系统总体安全指标, 其中m为系统数据流种类数量 |
| ti | 第i种数据流的平均端到端时延 | |
| timelimiti | - | 时延限值 |
| ratei | 第i种数据流的超时率 | |
| αi | 超时率容忍度 | |
| timei | 数据流i的相对时延 | |
| time | maxtimei | 时间敏感数据流总体时延指标, 数据i为时间敏感(time-triggered, TT)流 |
| C | {cij} | 安全任务的选择矩阵 |
| ωs | - | 系统总体安全指标权重 |
| ωt | 时间敏感数据流总体时延指标权重 |
Table 5
Table 6
Types of data flows"
| 数据流种类 | 发送端 | 接收端 | 类别 | 优先级 | 数据帧大小/字节 | 周期/ms | 微突发性 | 时延限制/ms |
| 数控机床1传感器数据 | 数控机床1 | 控制器1 | TT | P7 | 50 | 5 | - | 3 |
| 数控机床2传感器数据 | 数控机床2 | 控制器2 | TT | P7 | 50 | 5 | - | 3 |
| 数控机床3传感器数据 | 数控机床3 | 控制器3 | TT | P7 | 50 | 5 | - | 3 |
| 数控机床4传感器数据 | 数控机床4 | 控制器4 | TT | P7 | 50 | 5 | - | 3 |
| 控制器1控制指令 | 控制器1 | 数控机床1 | TT | P7 | 50 | 5 | - | 3 |
| 控制器2控制指令 | 控制器2 | 数控机床2 | TT | P7 | 50 | 5 | - | 3 |
| 控制器3控制指令 | 控制器3 | 数控机床3 | TT | P7 | 50 | 5 | - | 3 |
| 控制器4控制指令 | 控制器4 | 数控机床4 | TT | P7 | 50 | 5 | - | 3 |
| 工业摄像机1音视频流 | 工业摄像机1 | 操作面板 | AVB | P5 | 1 518 | 100 | 每100 ms发送200个数据帧 | 20 |
| 工业摄像机2音视频流 | 工业摄像机2 | 操作面板 | AVB | P5 | 1 518 | 100 | 每100 ms发送200个数据帧 | 20 |
| 操作面板工序指令 | 操作面板 | 控制器(1, 2, 3, 4) | BE | P1 | 1 000 | 1 000 | - | 1 000 |
Table 6
Table 11
Task arrangement results"
| 数据流 | 安全任务 |
| 数控机床1传感器数据 | RSA-1 024加/解密、RSA-1 024数字签名/认证、流量过滤2 |
| 数控机床2传感器数据 | DES加/解密、RSA-2 048数字签名/认证、流量过滤1 |
| 数控机床3传感器数据 | AES加/解密、RSA-4 096数字签名/认证、流量过滤1 |
| 数控机床4传感器数据 | RSA-2 048加/解密、RSA-1 024数字签名/认证、流量过滤1 |
| 控制器1控制指令 | AES加/解密、RSA-4 096数字签名/认证 |
| 控制器2控制指令 | RSA-1 024加/解密、RSA-4 096数字签名/认证 |
| 控制器3控制指令 | RSA-2 048加/解密、RSA-2 048数字签名/认证 |
| 控制器4控制指令 | AES加/解密、RSA-4 096数字签名/认证 |
| 工业摄像机1音视频流 | AES加/解密、RSA-1 024数字签名/认证、流量过滤1 |
| 工业摄像机2音视频流 | AES加/解密、RSA-1 024数字签名/认证、流量过滤2 |
| 操作面板工序指令 | RSA-1 024加/解密、RSA-2 048数字签名/认证、流量过滤1 |
Table 11
| 1 | IEC 61508-2010. International electro technical commission. Functional safety of electrical electronic programmable electronic safety-related systems[S]. Geneva: International Electro Technical Commission, 2010. |
| 2 | IEC62443-3-3. International electro technical commission. Industrial communication networks-network and system security[S]. Geneva: International Electrotechnical Commission, 2013. |
| 3 | KRIAA S , PIETRE-CAMBACEDES L , BOUISSOU M , et al. A survey of approaches combining safety and security for industrial control systems[J]. Reliability Engineering & System Safety, 2015, 139, 156- 178. |
| 4 | STONEBURNER G . Toward a unified security-safety model[J]. Computer, 2006, 39 (8): 96- 97. |
| 5 | EAMES D P, MOFFETT J. The integration of safety and security requirements[C]//Proc. of the 18th International Conference on Computer Safety, Reliability and Security, 1999: 468-480. |
| 6 | XIONG W Z, JIN J H. Summary of integrated application of functional safety and information security in industry[C]//Proc. of the 12th International Conference on Reliability, Maintain-ability, and Safety, 2018: 463-469. |
| 7 | HOLLERER S, KASTNER W, SAUTER T. Towards a comprehensive ontology considering safety, security, and operation requirements in OT[C]//Proc. of the 28th International Conference on Emerging Technologies and Factory Automation, 2023. |
| 8 | MENON C, VIDALIS S. Towards the resolution of safety and security conflicts[C]//Proc. of the International Carnahan Conference on Security Technology, 2021. |
| 9 | ZHOU C J , LI X , YANG S H , et al. Risk-based scheduling of security tasks in industrial control systems with consideration of safety[J]. IEEE Trans.on Industrial Informatics, 2019, 16 (5): 3112- 3123. |
| 10 | 胡博文, 周纯杰, 刘璐. 基于模糊多目标决策的智能仪表功能安全与信息安全融合方法[J]. 信息网络安全, 2021, 21 (7): 10- 16. |
| HU B W , ZHOU C J , LIU L . Coordination of functional safety and information security for intelligent instrument based on fuzzy multi-objective decision[J]. Netinfo Security, 2021, 21 (7): 10- 16. | |
| 11 | 靳江红, 莫昌瑜, 李刚. 工业控制系统功能安全与信息安全一体化防护措施研究[J]. 工业安全与环保, 2020, 46 (1): 53- 60. |
| JIN J H , MO C Y , LI G . Integration technology of functional safety and cyber security for industrial control system[J]. Industrial Safety and Environmental Protection, 2020, 46 (1): 53- 60. | |
| 12 | LEIVADEAS A , FALKNER M , LAMBADARIS I , et al. Optimal virtualized network function allocation for an SDN enabled cloud[J]. Computer Standards & Interfaces, 2017, 54, 266- 278. |
| 13 |
PAXSON V , FLOYD S . Wide area traffic: the failure of Poi-sson modeling[J]. IEEE/ACM Trans.on Networking,, 1995, 3 (3): 226- 244.
doi: 10.1109/90.392383 |
| 14 | 刘艺. 面向SDN网络的安全服务链映射与调整方法研究[D]. 郑州: 中国人民解放军战略支援部队信息工程大学, 2019. |
| LIU Y. Research on security service chain embedding and adjusting methods oriented to SDN network[D]. Zhengzhou: Information Engineering University, 2019. | |
| 15 | 黄睿, 张红旗. 安全服务链中虚拟网络功能分配与调度算法研究[J]. 计算机应用研究, 2019, 36 (3): 257- 262. |
| HUANG R , ZHANG H Q . Research on algorithm of VNF allocation and scheduling problems in security service chain[J]. Application Research of Computers, 2019, 36 (3): 257- 262. | |
| 16 | 张奇. 基于SDN/NFV的安全服务链自动编排部署框架[J]. 计算机系统应用, 2018, 27 (3): 198- 204. |
| ZHANG Q . Automatic scheduling deployment framework for security service chain based on SDN/NFV[J]. Computer Systems & Applications, 2018, 27 (3): 198- 204. | |
| 17 | 王泽南, 李佳浩, 檀朝红, 等. 面向网络安全资源池的智能服务链系统设计与分析[J]. 网络与信息安全学报, 2022, 8 (4): 175- 181. |
| WANG Z N , LI J H , TAN C H , et al. Design and analysis of intelligent service chain system for network security resource pool[J]. Chinese Journal of Network and Information Security, 2022, 8 (4): 175- 181. | |
| 18 | 刘璐, 朱越, 郭伟杰, 等. 工业互联网环境下智能仪表安全任务一体化调度方法研究[J]. 信息安全研究, 2023, 9 (4): 321- 330. |
| LIU L , ZHU Y , GUO W J , et al. Research on integrated scheduling method of safety and security tasks for intelligent instruments in industrial internet[J]. Journal of Information Security Research, 2023, 9 (4): 321- 330. | |
| 19 | IEEE 802.1 Working Group . IEEE standard for local and metropolitan area networks-timing and synchronization for time-sensitive applications[J]. IEEE Std 802.1 AS-2020 (Revision of IEEE Std 802.1 AS-2011), 2020, 1- 421. |
| 20 | IEEE 802.1 Working Group. . IEEE standard for local and met-ropolitan area networks-bridges and bridged networks-amendment 25: Enhancements for Scheduled Traffic[J]. IEEE Std, 2016, 802, 1- 57. |
| 21 | KONTRON S&T GROUP. Time-sensitive networking(TSN)[EB/OL]. [2024-02-26]. https://www.kontron.com/resources/collateral/white_papers/kontron_wp_tsn_en_2022.pdf?product=151637. |
| 22 | 工业互联网产业联盟. 工业互联网时间敏感网络(TSN)产业白皮书[EB/OL]. [2024-02-26]. https://www.aii-alliance.org/upload/202009/0901_165010_961.pdf. |
| Industrial Internet Industry Alliance. Industrial internet time-sensitive networking (TSN) industry white paper[EB/OL]. [2024-02-26]. https://www.aii-alliance.org/upload/202009/0901_165010_961.pdf. | |
| 23 | 卜天宇, 严锦立, 黄金锋, 等. 面向OPC UA/TSN架构的工业控制网络安全防护研究[J]. 网络空间安全, 2019, 10 (10): 93- 100. |
| BU T Y , YAN J L , HUANG J F , et al. Research on industrial control network security protection based on OPC UA/TSN architecture[J]. Cyberspace Security, 2019, 10 (10): 93- 100. | |
| 24 | WANG H W, LI X G, HU X Y. A vulnerability mining method for IEEE 802.1QBV in TSN system based on timed automata[C]// Proc. of the China Automation Congress, 2022: 6644-6649. |
| 25 | PEÑA R A, PASCUAL M, ASTARLOA A, et al. Impact of MACsec security on TSN traffic[C]//Proc. of the 37th Conference on Design of Circuits and Integrated Circuits, 2022. |
| 26 | DIK D, LARSEN I, BERGER M S. MACsec and AES-GCM hardware architecture with frame preemption support for transport security in time sensitive networking[C]//Proc. of the International Conference on Computer, Information and Telecommunication Systems, 2023. |
| 27 |
SETHI R , KADAM A , PRABHU K , et al. Security considerations to enable time-sensitive networking over 5G[J]. IEEE Open Journal of Vehicular Technology, 2022, 3, 399- 407.
doi: 10.1109/OJVT.2022.3205014 |
| 28 |
LI H X , LI D K , ZHANG X D , et al. A security management architecture for time synchronization towards high precision networks[J]. IEEE Access, 2021, 9, 117542- 117553.
doi: 10.1109/ACCESS.2021.3107203 |
| 29 | ZHANG Y J, XU Q M, CHEN C L, et al. SvTI: SFC-driven queue injection in virtual time-sensitive network via augmented topology[C]//Proc. of the Globecom IEEE Global Communications Conference, 2022: 4916-4921. |
| 30 | 张吉军. 模糊层次分析法(FAHP)[J]. 模糊系统与数学, 2000, 14 (2): 80- 88. |
| ZHANG J J . Fuzzy analytic hierarchy process (FAHP)[J]. Fuzzy Systems and Mathematics, 2000, 14 (2): 80- 88. | |
| 31 | 何明, 郑翔, 赖海光, 等. 蒙特卡罗方法在网络性能仿真中的应用[J]. 系统仿真学报, 2009, 21 (24): 7770- 7772. |
| HE M , ZHENG X , LAI H G , et al. Application in network performance simulation with Monte Carlo method[J]. Journal of System Simulation, 2009, 21 (24): 7770- 7772. |
| [1] | Kexin BI, Minggong WU, Xiangxi WEN, Wenbin ZHANG, Wenda YANG. Conflict resolution strategy based on flight conflict network and genetic algorithm [J]. Systems Engineering and Electronics, 2023, 45(5): 1429-1440. |
| [2] | Chengzhao LU, Jianxing GONG, Lei ZHU, Quan LIU. Research on task scheduling algorithm in resource-constrained environments [J]. Systems Engineering and Electronics, 2021, 43(12): 3586-3593. |
| [3] | Honghong ZHANG, Xusheng GAN, Ang LI, Zhiqiang GAO, Xinyu XU. UAV obstacle avoidance and track recovery strategy based onvelocity obstacle method [J]. Systems Engineering and Electronics, 2020, 42(8): 1759-1767. |
| [4] | Jiayi LIU, Shaohua YUE, Gang WANG, Jie ZHANG, Xiaoqiang YAO. Design of command control model based on MPC-MAS under multi-platform distributed cooperative operation [J]. Systems Engineering and Electronics, 2020, 42(7): 1582-1589. |
| [5] | WU Minggong, WANG Zekun, WEN Xiangxi, JIANG Xurui, SUN Qianrui. Aircraft conflict resolution model based on geometric optimization [J]. Systems Engineering and Electronics, 2019, 41(4): 863-869. |
| [6] | FU Xiaowei, FENG Peng, GAO Xiaoguang, LIU Zhong. Conflict resolution in multi-UAV cooperative tasks assignment withcommunication delay [J]. Systems Engineering and Electronics, 2018, 40(7): 1491-1497. |
| [7] | JIANG Xurui, WU Minggong, WEN Xiangxi, TU Congliang, NIE Dangmin. Conflict resolution of multi-aircraft based on the cooperative game [J]. Systems Engineering and Electronics, 2018, 40(11): 2482-. |
| [8] | WANG Hai-bo, XU Min-qiang, WANG Ri-xin, LI Yu-qing. Long-term acquisition plan method for small satellites constellation [J]. Journal of Systems Engineering and Electronics, 2011, 33(6): 1293-1298. |
| [9] | YANG Ping, LIU Wei-dong, BI Yi-ming. Goal conflict resolution of multi-agent systems based on distributed negotiation evolution algorithm [J]. Journal of Systems Engineering and Electronics, 2009, 31(8): 1918-1922. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||