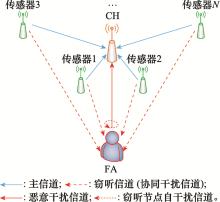
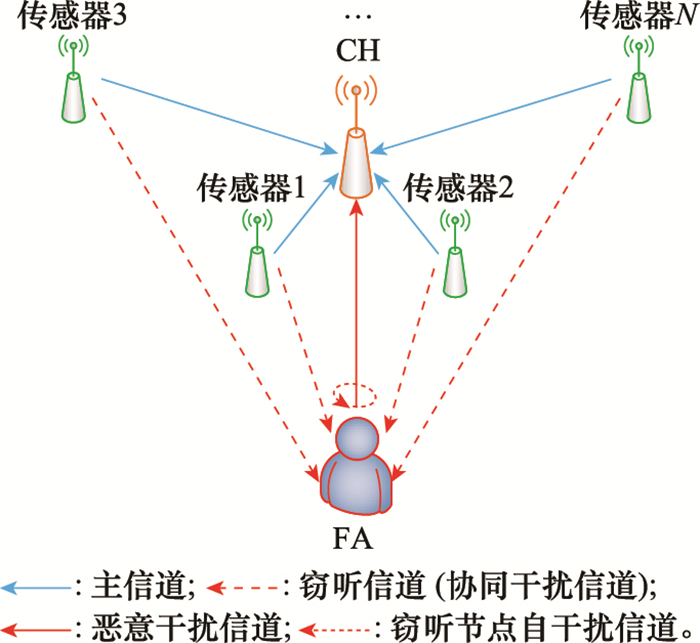
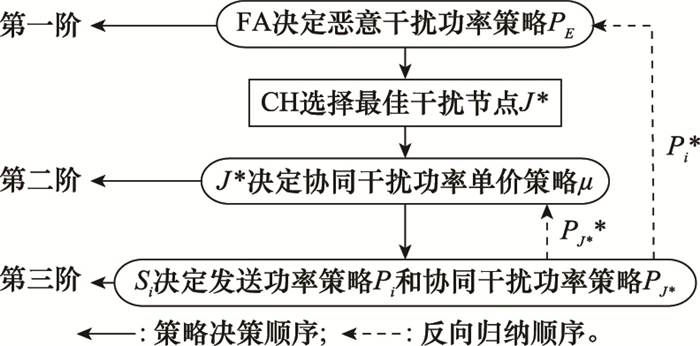
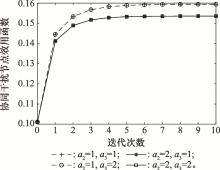
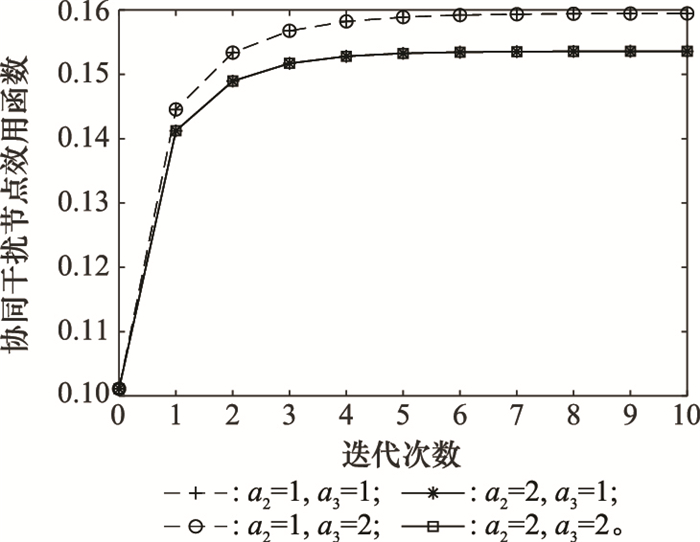
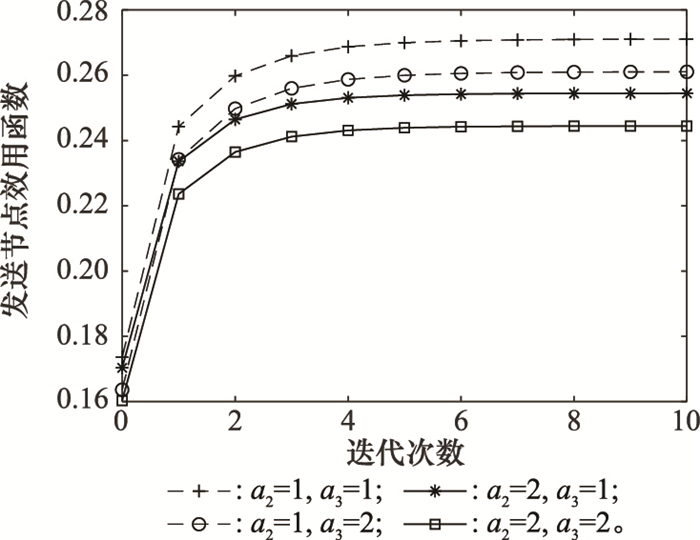
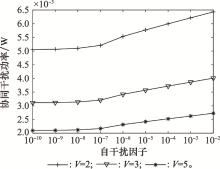
Systems Engineering and Electronics ›› 2021, Vol. 43 ›› Issue (10): 2931-2939.doi: 10.12305/j.issn.1001-506X.2021.10.28
• Systems Engineering • Previous Articles Next Articles
Multi-level Stackelberg game model against full-duplex attacking node in IWSN physical layer
Chonglin HE1, Ziwen SUN1,2,*
- 1. School of Internet of Things, Jiangnan University, Wuxi 214122, China
2. Engineering Research Center of Internet of Things Technology Applications Ministry of Education, Wuxi 214122, China
-
Received:2020-09-13Online:2021-10-01Published:2021-11-04 -
Contact:Ziwen SUN
CLC Number:
Cite this article
Chonglin HE, Ziwen SUN. Multi-level Stackelberg game model against full-duplex attacking node in IWSN physical layer[J]. Systems Engineering and Electronics, 2021, 43(10): 2931-2939.
share this article
Table 1
Description of symbols used"
| 符号 | 说明 |
| CH | 簇头节点 |
| Si | 第i个传感器节点 |
| J | 协作干扰节点 |
| YCH | 簇头节点接收的信号 |
| YA | 全双工主动攻击节点接收信号 |
| FA | 全双工攻击节点 |
| Xi | 发送节点发送信号 |
| XJ | 协作干扰节点协作干扰信号 |
| XA | FA恶意干扰信号 |
| Pi | 发送节点发送功率 |
| PJ | 协作干扰节点协作干扰功率 |
| PA | FA恶意干扰功率 |
| Hi, CH | Si到CH的信道增益 |
| HJ, CH | J到CH的信道增益 |
| HA, CH | FA到CH的信道增益 |
| Hi, A | Si到FA的信道增益 |
| HJ, A | J到FA的信道增益 |
| HA, A | FA自干扰信道增益 |
| N0 | 所有节点端的热噪声 |
| Ci, CH | Si到CH的主信道容量 |
| Ci, A | Si到FA的窃听信道容量 |
Table 1
| 1 | QUEIROZ D V , ALENCAR M S , GOMES R D , et al. Survey and systematic mapping of industrial wireless sensor networks[J]. Journal of Network and Computer Applications, 2017, 97 (11): 96- 125. |
| 2 |
CHETTRI L , BERA R . A comprehensive survey on internet of things (IoT) toward 5G wireless systems[J]. IEEE Internet of Things Journal, 2020, 7 (1): 16- 32.
doi: 10.1109/JIOT.2019.2948888 |
| 3 |
SALAM H A , KHAN B M . IWSN-standards, challenges and future[J]. IEEE Potentials, 2016, 35 (2): 9- 16.
doi: 10.1109/MPOT.2015.2422931 |
| 4 |
JING Q , VASILAKOS A Y , WAN J , et al. Security of the internet of things: perspectives and challenges[J]. Wireless Networks, 2014, 20 (8): 2481- 2501.
doi: 10.1007/s11276-014-0761-7 |
| 5 |
ZOU Y , WANG G . Intercept behavior analysis of industrial wireless sensor networks in the presence of eavesdropping attack[J]. IEEE Trans.on Industrial Informatic, 2016, 12 (2): 780- 787.
doi: 10.1109/TII.2015.2399691 |
| 6 |
TOMIC I , MCCANN J A . A survey of potential security issues in existing wireless sensor network protocols[J]. IEEE Internet of Things Journal, 2017, 4 (6): 1910- 1923.
doi: 10.1109/JIOT.2017.2749883 |
| 7 |
WYNER A D . The wire-tap channel[J]. Bell Systems Techno-logy Journal, 1975, 54 (8): 1355- 1387.
doi: 10.1002/j.1538-7305.1975.tb02040.x |
| 8 |
HAMAMREH J M , FURQAN H M , ARSLAN H . Classifications and applications of physical layer security techniques for confidentiality: a comprehensive survey[J]. IEEE Communications Surveys and Tutorials, 2019, 21 (2): 1773- 1828.
doi: 10.1109/COMST.2018.2878035 |
| 9 |
WU Y , KHISTI A , XIAO C , et al. A survey of physical layer security techniques for 5G wireless networks and challenges ahead[J]. IEEE Journal on Selected Areas in Communications, 2018, 36 (4): 679- 695.
doi: 10.1109/JSAC.2018.2825560 |
| 10 |
朱江, 汪智豪. 时间反演联合接收端人工噪声的安全传输方案[J]. 系统工程与电子技术, 2020, 42 (10): 2374- 2380.
doi: 10.3969/j.issn.1001-506X.2020.10.28 |
|
ZHU J , WANG Z H . Secure transmission scheme of time reversal combined with artificial noise at receiver[J]. Systems Engineering and Electronics, 2020, 42 (10): 2374- 2380.
doi: 10.3969/j.issn.1001-506X.2020.10.28 |
|
| 11 | JAMEEL F , WYNE S , KADDOUM G , et al. A comprehensive survey on cooperative relaying and jamming strategies for physical layer security[J]. IEEE Communications Surveys & Tutorials, 2018, 21 (3): 2734- 2771. |
| 12 | HU L , WEN H , WU B , et al. Cooperative jamming for physical layer security enhancement in internet of things[J]. IEEE Internet of Things Journal, 2017, 5 (1): 219- 228. |
| 13 |
VO V N , NGUYEN T G , SO-IN C , et al. Secrecy outage performance analysis for energy harvesting sensor networks with a jammer using relay selection strategy[J]. IEEE Access, 2018, 6, 23406- 23419.
doi: 10.1109/ACCESS.2018.2829485 |
| 14 | YANG M Q , ZHANG B N , HUANG Y Z , et al. Secure multiuser communications in wireless sensor networks with TAS and cooperative jamming[J]. Sensors, 2014, 16 (11): 1908. |
| 15 | PTR P H. A primer in game theory[M]. Harvester Wheatsheaf, 1992. |
| 16 | NAMVAR N, SAAD W, BAHADORI N, et al. Jamming in the internet of things: a game-theoretic perspective[C]//Proc. of the Global Communications Conference, 2016. |
| 17 | JIANG G X , SHEN S G , HU K L , et al. Evolutionary game-based secrecy rate adaptation in wireless sensor networks[J]. International Journal of Distributed Sensor Networks, 2015, 2015 (25): 975454. |
| 18 | 杜晓丽, 梁开荣, 李登峰. 基于CIS值的双边链路形成策略优化两型博弈方法[J]. 系统工程与电子技术, 2020, 42 (7): 1550- 1557. |
| DU X L , LIANG K R , LI D F . Biform game approach to strategy optimization of bilateral link formation based on CIS value[J]. Systems Engineering and Electronics, 2020, 42 (7): 1550- 1557. | |
| 19 | ROMERO E , BLESA J , ARAUJO A . An adaptive energy aware strategy based on game theory to add privacy in the physical layer for Cognitive WSNs[J]. Ad Hoc Networks, 2018, 92, 102414. |
| 20 |
WANG K , YUAN L , MIYAZAKI T , et al. Jamming and eavesdropping defense in green cyber-physical transportation systems using stackelberg game[J]. IEEE Trans.on Industrial Informatics, 2018, 14 (9): 4232- 4242.
doi: 10.1109/TII.2018.2841033 |
| 21 | ZHANG R, SONG L, HAN Z, et al. Improve physical layer security in cooperative wireless network using distributed auction games[C]//Proc. of the Computer Communications Workshops, 2011: 18-23. |
| 22 |
ZHOU H , HE D X , WANG H . Joint relay and jammer selection for secure cooperative networks with a full-duplex active eavesdropper[J]. IET Communications, 2020, 14 (6): 1043- 1055.
doi: 10.1049/iet-com.2019.1042 |
| 23 | 何崇林, 孙子文. 多跳IWSN物理层安全的Stackelberg博弈[J]. 信号处理, 2021, 37 (4): 578- 587. |
| HE C L , SUN Z W . Stackelberg game for physical layer security of multi-hop IWSN[J]. Journal of Signal Processing, 2021, 37 (4): 578- 587. | |
| 24 |
LI C X , LIU Y , XU Q , et al. Self-interference cancellation with frequency offset and nonlinear distortion suppression for cooperative jamming communications[J]. IEEE Communications Letters, 2019, 23 (11): 2091- 2094.
doi: 10.1109/LCOMM.2019.2936845 |
| 25 |
LEUNGYC S , HELLMAN M . The Gaussian wire-tap channel[J]. IEEE Trans.on Information Theory, 1978, 24 (4): 451- 456.
doi: 10.1109/TIT.1978.1055917 |
| 26 |
WU R J , VANGORDER R A . Nonlinear dynamics of discrete time multi-level leader-follower games[J]. Applied Mathema-tics and Computation, 2018, 320, 240- 250.
doi: 10.1016/j.amc.2017.09.034 |
| 27 |
FANG H , XU L , ZOU Y L , et al. Three-stage Stackelberg game for defending against full-duplex active eavesdropping attacks in cooperative communication[J]. IEEE Trans.on Vehicular Technology, 2018, 67 (11): 10788- 10799.
doi: 10.1109/TVT.2018.2868900 |
| 28 | 金鑫. 无线信道传播模型的研究与实现[D]. 北京: 北京邮电大学, 2010. |
| JIN X. Research and implentation of wireless channel propagation modle[D]. Beijing: Beijing University of Posts and Telecommunications, 2010. | |
| 29 |
ZOU Y L , WANG X B , SHEN W M . Optimal relay selection for physical-layer security in cooperative wireless networks[J]. IEEE Journal on Selected Areas in Communications, 2013, 31 (10): 2099- 2111.
doi: 10.1109/JSAC.2013.131011 |
| 30 |
BASSILY R , ULUKUS S . Deaf cooperation and relay selection strategies for secure communication in multiple relay networks[J]. IEEE Trans.on Signal Processing, 2013, 61 (6): 1544- 1554.
doi: 10.1109/TSP.2012.2235433 |
| 31 |
WANG K , YUAN L , MIYAZAKI T , et al. Strategic antieavesdropping game for physical layer security in wireless cooperative networks[J]. IEEE Trans.on Vehicular Technology, 2017, 66 (10): 9448- 9457.
doi: 10.1109/TVT.2017.2703305 |
| 32 | DUAN B W, CAI Y M, ZHENG J C, et al. Cooperative jammer power allocation-A Nash bargaining solution method[C]//Proc. of the International Conference on Wireless Communications & Signal Processing, 2015. |
| 33 |
KIM T S , KIM S L . Random power control in wireless ad hoc networks[J]. IEEE Communications Letters, 2005, 9 (12): 1046- 1048.
doi: 10.1109/LCOMM.2005.1576583 |
| [1] | Xiaorong JING, Zhenyuan SONG, Yue LUO, Yudan MA. Design of physical layer safety scheme aided with IRS and artificial noise for MIMO communication systems [J]. Systems Engineering and Electronics, 2022, 44(10): 3266-3274. |
| [2] | Danyu DIAO, Buhong WANG, Kunrui CAO, Runze DONG, Tianhao CHENG. Secrecy performance analysis of UAV-based communications against full-duplex eavesdropping [J]. Systems Engineering and Electronics, 2022, 44(1): 313-319. |
| [3] | Bing FANG, Bing HAN. Secure beamforming method for the MISO SWIPT system [J]. Systems Engineering and Electronics, 2021, 43(6): 1692-1698. |
| [4] | Chenwei GU, Zhi LIN, Min LIN, Luyao XIE, Jian OUYANG, Shuo HUANG. Robust secure beamforming design for the downlink of satellite communications [J]. Systems Engineering and Electronics, 2021, 43(5): 1361-1370. |
| [5] | Weijia LEI, Yuyu LI. Double scrambling scheme for reducing security gap of channel codes [J]. Systems Engineering and Electronics, 2020, 42(2): 458-465. |
| [6] | FU Xiaomei, CHEN Li, CHANG Shuai. Prediction of untrusted relay behavior based on physical layer security features [J]. Systems Engineering and Electronics, 2018, 40(3): 671-675. |
| [7] | YUAN Tian, TAO Jianfeng, LI Xingcheng. Main lobe track deception jamming method based on association rule [J]. Systems Engineering and Electronics, 2018, 40(2): 273-279. |
| [8] | . Synthesis algorithm of directional modulation signals based on sparse arrays [J]. Systems Engineering and Electronics, 2018, 40(12): 2816-2823. |
| [9] | LEI Weijia, YANG Xiaoyan, LIN Xiuzhen. Secure transmission scheme based on SWIPT relay with antenna grouping [J]. Systems Engineering and Electronics, 2017, 39(8): 1849-1856. |
| [10] | FU Xiao-mei, YAO Xiao-ming, ZONG Qun. Relay selection and power optimization in cooperative coalitions [J]. Systems Engineering and Electronics, 2016, 38(5): 1176-. |
| [11] | WANG Shu, DA Xin-yu, CHU Zhen-yong. Wiretapping strategies for artificial noise assisted communication in MU-MIMO system [J]. Systems Engineering and Electronics, 2016, 38(11): 2648-2652. |
| [12] | HONG Tao, LI Zhi-peng. Research of the peak-to-average power ratio problem for physical-layer security communication system aided by artificial noise [J]. Systems Engineering and Electronics, 2016, 38(11): 2653-2659. |
| [13] | ZHANG Yang-rui, GAO Mei-guo, LUO Hao-yue, LI Yun-jie. Evaluation method of cooperative jamming effect on radar net based on detection probability [J]. Systems Engineering and Electronics, 2015, 37(8): 1778-1786. |
| [14] | LEI Wei-jia, JIANG Xue, ZUO Li-jie, XIE Xian-zhong. Secrecy rate optimization for two-hop relay system with energy#br# harvesting based on cooperative jamming [J]. Systems Engineering and Electronics, 2015, 37(12): 2835-2841. |
| [15] | ZHANG Yang-rui, GAO Mei-guo, LI Yun-jie. Performance of cooperative suppress jamming on LFM pulsed radar’s ML-CFAR detection [J]. Systems Engineering and Electronics, 2014, 36(11): 2156-2163. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||